Creating a web server on a cloud: Difference between revisions
(updating links) |
|||
| (14 intermediate revisions by 4 users not shown) | |||
| Line 2: | Line 2: | ||
<translate> | <translate> | ||
<!--T:1--> | <!--T:1--> | ||
<i>Parent page: [[Cloud]]</i> | |||
<!--T:2--> | <!--T:2--> | ||
This page describes the simplest case of creating a web server on | This page describes the simplest case of creating a web server on our clouds using Ubuntu Linux and the Apache web server. | ||
=Security considerations= <!--T:3--> | =Security considerations= <!--T:3--> | ||
Any time you make a computer accessible to the public, security must be considered. | Any time you make a computer accessible to the public, security must be considered. <i>Accessible to the public</i> could mean allowing SSH connections, displaying HTML via HTTP, or using 3rd party software to provide a service (e.g. WordPress). Services such as SSH or HTTP are provided by programs called [https://en.wikipedia.org/wiki/Daemon_(computing) "daemons"], which stay running all the time on the computer and respond to outside requests on specific [https://en.wikipedia.org/wiki/Port_(computer_networking) ports]. With [[Managing_your_cloud_resources_with_OpenStack | OpenStack]], you can manage and restrict access to these ports, including granting access only to a specific [https://en.wikipedia.org/wiki/IP_address IP address] or to ranges of IP addresses; see [[Managing_your_cloud_resources_with_OpenStack#Security groups | Security groups]]. Restricting access to your VM will improve its security. However, restricting access does not necessarily remove all security vulnerabilities. If we do not use some sort of encryption when sending data (e.g. passwords), an eavesdropper can read that information. [https://en.wikipedia.org/wiki/Transport_Layer_Security Transport Layer Security] is the common way to encrypt this data, and any website which uses logins (e.g. WordPress, MediaWiki) should use it; see [[Configuring Apache to use SSL]]. It is also possible that data transmitted from your web server to a client could be modified on the way by a third party if you are not encrypting it. While this might not directly cause issues for your web server, it can for your clients. In most cases it is recommended to use encryption on your web server. You are responsible for the security of your virtual machines and should take this seriously. | ||
=Installing Apache= <!--T:5--> | =Installing Apache= <!--T:5--> | ||
| Line 14: | Line 14: | ||
<!--T:9--> | <!--T:9--> | ||
# Create a persistent virtual machine (see [[Working_with_volumes#Booting_from_a_volume | Booting from a volume]]) running Ubuntu Linux by following the [[Cloud Quick Start]] instructions. | # Create a persistent virtual machine (see [[Working_with_volumes#Booting_from_a_volume | Booting from a volume]]) running Ubuntu Linux by following the [[Cloud Quick Start]] instructions. | ||
# Open port 80 to allow HTTP requests into your VM by following [[Cloud_Quick_Start#Connecting_to_your_VM_with_SSH | these instructions]] but selecting HTTP | # Open port 80 to allow HTTP requests into your VM by following [[Cloud_Quick_Start#Connecting_to_your_VM_with_SSH | these instructions]] but selecting HTTP from the drop-down box instead of SSH. | ||
# While logged into your VM | # While logged into your VM: | ||
## Update your apt-get repositories with the command {{Command|sudo apt-get update}} | ## Update your apt-get repositories with the command {{Command|sudo apt-get update}} | ||
## Upgrade Ubuntu to the latest version with the command {{Command|sudo apt-get upgrade}} Upgrading to the latest version of Ubuntu ensures your VM has the latest security patches. | ## Upgrade Ubuntu to the latest version with the command {{Command|sudo apt-get upgrade}} Upgrading to the latest version of Ubuntu ensures your VM has the latest security patches. | ||
## Install Apache web server with the command{{Command|sudo apt-get install apache2}} | ## Install the Apache web server with the command{{Command|sudo apt-get install apache2}} | ||
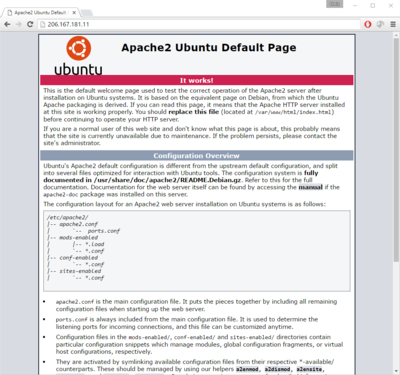
# [[File:Apache2-test-page.png|400px|thumb| Apache2 test page (Click for larger image)]] Go to the newly created temporary Apache | # [[File:Apache2-test-page.png|400px|thumb| Apache2 test page (Click for larger image)]] Go to the newly created temporary Apache web page by entering the floating IP address of your VM into your browser's address bar. This is the same IP address you use to connect to your VM with SSH. You should see something similar to the Apache2 test page shown to the right. | ||
# Start modifying the content of the files in <code>/var/www/html</code> to create your website, specifically the index.html file, which is the entry point for your newly created website. | # Start modifying the content of the files in <code>/var/www/html</code> to create your website, specifically the index.html file, which is the entry point for your newly created website. | ||
==Change web server's root directory== <!--T:6--> | ==Change the web server's root directory== <!--T:6--> | ||
It is often much easier to manage a website if the files are owned by the user who is connecting to the VM. In the case of the Ubuntu image we're using in this example, this is user < | It is often much easier to manage a website if the files are owned by the user who is connecting to the VM. In the case of the Ubuntu image we're using in this example, this is user <code>ubuntu</code>. Follow these steps to direct Apache to serve files from <code>/home/ubuntu/public_html</code>, for example, instead of from <code>/var/www/html</code>. | ||
# Use the command{{Command|sudo vim /etc/apache2/apache2.conf}} (or some other editor) to change the line <code><Directory /var/www/></code> to <code><Directory /home/ubuntu/public_html></code> | # Use the command{{Command|sudo vim /etc/apache2/apache2.conf}} (or some other editor) to change the line <code><Directory /var/www/></code> to <code><Directory /home/ubuntu/public_html></code> | ||
# Use the command{{Command|sudo vim /etc/apache2/sites-available/000-default.conf}} to edit the line <code>DocumentRoot /var/www/html</code> to become <code>DocumentRoot /home/ubuntu/public_html</code> | # Use the command{{Command|sudo vim /etc/apache2/sites-available/000-default.conf}} to edit the line <code>DocumentRoot /var/www/html</code> to become <code>DocumentRoot /home/ubuntu/public_html</code> | ||
# Create the directory in the | # Create the directory in the Ubuntu user's home directory with {{Command|mkdir public_html}} | ||
# Copy the default page into the directory with {{Command|cp /var/www/html/index.html /home/ubuntu/public_html}} | # Copy the default page into the directory with {{Command|cp /var/www/html/index.html /home/ubuntu/public_html}} | ||
# Then restart the Apache server for these changes to take effect with {{Command|sudo service apache2 restart}} | # Then restart the Apache server for these changes to take effect with {{Command|sudo service apache2 restart}} | ||
You should now be able to edit the file <code>/home/ubuntu/public_html/index.html</code> without using <code>sudo</code>. Any changes you make should be visible if you refresh the page you loaded into your browser in the previous section. | You should now be able to edit the file <code>/home/ubuntu/public_html/index.html</code> without using <code>sudo</code>. Any changes you make should be visible if you refresh the page you loaded into your browser in the previous section. | ||
=Limiting | =Limiting bandwidth= <!--T:10--> | ||
If your | If your web server is in high demand, it is possible that it may use considerable bandwidth resources. A good way to limit overall bandwidth usage of your Apache web server is to use the [https://github.com/IvnSoft/mod_bw Apache bandwidth module]. | ||
== Installing == | == Installing == | ||
{{Command|sudo apt install libapache2-mod-bw}} | {{Command|sudo apt install libapache2-mod-bw}} | ||
| Line 39: | Line 39: | ||
An example configuration to limit total bandwidth from all clients to 100Mbps is | An example configuration to limit total bandwidth from all clients to 100Mbps is | ||
<!--T:11--> | |||
BandWidthModule On | BandWidthModule On | ||
ForceBandWidthModule On | ForceBandWidthModule On | ||
| Line 51: | Line 51: | ||
<!--T:12--> | <!--T:12--> | ||
This should be placed between the <code><VirtualHost></VirtualHost></code> tags for your site. The default | This should be placed between the <code><VirtualHost></VirtualHost></code> tags for your site. The default Apache site configuration is in the file <code>/etc/apache2/sites-enabled/000-default.conf</code>. | ||
=Where to go from here= <!--T:7--> | =Where to go from here= <!--T:7--> | ||
| Line 59: | Line 59: | ||
<!--T:8--> | <!--T:8--> | ||
[[Category: | [[Category:Cloud]] | ||
</translate> | </translate> | ||
Latest revision as of 19:09, 15 July 2024
Parent page: Cloud
This page describes the simplest case of creating a web server on our clouds using Ubuntu Linux and the Apache web server.
Security considerations[edit]
Any time you make a computer accessible to the public, security must be considered. Accessible to the public could mean allowing SSH connections, displaying HTML via HTTP, or using 3rd party software to provide a service (e.g. WordPress). Services such as SSH or HTTP are provided by programs called "daemons", which stay running all the time on the computer and respond to outside requests on specific ports. With OpenStack, you can manage and restrict access to these ports, including granting access only to a specific IP address or to ranges of IP addresses; see Security groups. Restricting access to your VM will improve its security. However, restricting access does not necessarily remove all security vulnerabilities. If we do not use some sort of encryption when sending data (e.g. passwords), an eavesdropper can read that information. Transport Layer Security is the common way to encrypt this data, and any website which uses logins (e.g. WordPress, MediaWiki) should use it; see Configuring Apache to use SSL. It is also possible that data transmitted from your web server to a client could be modified on the way by a third party if you are not encrypting it. While this might not directly cause issues for your web server, it can for your clients. In most cases it is recommended to use encryption on your web server. You are responsible for the security of your virtual machines and should take this seriously.
Installing Apache[edit]
- Create a persistent virtual machine (see Booting from a volume) running Ubuntu Linux by following the Cloud Quick Start instructions.
- Open port 80 to allow HTTP requests into your VM by following these instructions but selecting HTTP from the drop-down box instead of SSH.
- While logged into your VM:
- Update your apt-get repositories with the command
[name@server ~]$ sudo apt-get update
- Upgrade Ubuntu to the latest version with the command Upgrading to the latest version of Ubuntu ensures your VM has the latest security patches.
[name@server ~]$ sudo apt-get upgrade
- Install the Apache web server with the command
[name@server ~]$ sudo apt-get install apache2
- Update your apt-get repositories with the command
- Go to the newly created temporary Apache web page by entering the floating IP address of your VM into your browser's address bar. This is the same IP address you use to connect to your VM with SSH. You should see something similar to the Apache2 test page shown to the right.
- Start modifying the content of the files in
/var/www/htmlto create your website, specifically the index.html file, which is the entry point for your newly created website.
Change the web server's root directory[edit]
It is often much easier to manage a website if the files are owned by the user who is connecting to the VM. In the case of the Ubuntu image we're using in this example, this is user ubuntu. Follow these steps to direct Apache to serve files from /home/ubuntu/public_html, for example, instead of from /var/www/html.
- Use the command (or some other editor) to change the line
[name@server ~]$ sudo vim /etc/apache2/apache2.conf
<Directory /var/www/>to<Directory /home/ubuntu/public_html> - Use the command to edit the line
[name@server ~]$ sudo vim /etc/apache2/sites-available/000-default.conf
DocumentRoot /var/www/htmlto becomeDocumentRoot /home/ubuntu/public_html - Create the directory in the Ubuntu user's home directory with
[name@server ~]$ mkdir public_html
- Copy the default page into the directory with
[name@server ~]$ cp /var/www/html/index.html /home/ubuntu/public_html
- Then restart the Apache server for these changes to take effect with
[name@server ~]$ sudo service apache2 restart
You should now be able to edit the file /home/ubuntu/public_html/index.html without using sudo. Any changes you make should be visible if you refresh the page you loaded into your browser in the previous section.
Limiting bandwidth[edit]
If your web server is in high demand, it is possible that it may use considerable bandwidth resources. A good way to limit overall bandwidth usage of your Apache web server is to use the Apache bandwidth module.
Installing[edit]
[name@server ~]$ sudo apt install libapache2-mod-bw
[name@server ~]$ sudo a2enmod bw
Configuring[edit]
An example configuration to limit total bandwidth from all clients to 100Mbps is
BandWidthModule On ForceBandWidthModule On #Exceptions to badwith of 100Mbps should go here above limit #below in order to override it #limit all connections to 100Mbps #100Mbps *1/8(B/b)*1e6=12,500,000 bytes/s BandWidth all 12500000
This should be placed between the <VirtualHost></VirtualHost> tags for your site. The default Apache site configuration is in the file /etc/apache2/sites-enabled/000-default.conf.