Multifactor authentication: Difference between revisions
No edit summary |
No edit summary |
||
| Line 15: | Line 15: | ||
<!--T:21--> | <!--T:21--> | ||
You can choose any of these factors for this second authentication step: | You can choose any of these factors for this second authentication step: | ||
*Approving a notification on a smart device through the Duo Mobile application | *Approving a notification on a smart device through the Duo Mobile application. | ||
*Entering a code generated on demand | *Entering a code generated on demand. | ||
*Pushing a button on a hardware key (YubiKey). | *Pushing a button on a hardware key (YubiKey). | ||
<!--T:22--> | <!--T:22--> | ||
Revision as of 15:05, 26 April 2023
This article currently applies only to staff members: Multifactor authentication is still being tested by staff members. It will be made available to all users as an option at some later date.
Multifactor authentication (MFA) allows you to protect your account with more than a password. Once your account is configured to use this feature, you will need to enter your username and password as usual, and then perform a second action (the second factor) to access most of our services.
You can choose any of these factors for this second authentication step:
- Approving a notification on a smart device through the Duo Mobile application.
- Entering a code generated on demand.
- Pushing a button on a hardware key (YubiKey).
This feature will be progressively deployed, that is, it will not be immediately available for all our services.
Registering factors[edit]
Registering multiple factors[edit]
When you enable multifactor authentication for your account, we strongly recommend that you configure at least two options for your second factor. For example, you can use a phone and single-use codes; a phone and a hardware key; or two hardware keys. This will ensure that if you lose one factor, you can still use your other one to access your account.
To use a smartphone or tablet[edit]
- Install the Duo Mobile authentication application from the Apple Store or on Google Play
- Go to the CCDB, connect to your account and select My account → Multifactor authentication management.
- Under Register a device, click on Duo Mobile.
- Enter a name for your device.
- In the Duo Mobile application, click the "+" sign to add a new account, and scan the QR code that is shown to you.
To use a YubiKey[edit]
A YubiKey is a hardware token made by the Yubico company. If you do not have a smartphone or tablet, do not wish to use your phone or tablet for multifactor authentication, or are often in a situation when using your phone or tablet is not possible, then a YubiKey is your best option.
A YubiKey is the size of a small USB stick and costs between $50 and $100. Different models can fit in USB-A, USB-C, or Lightning ports, and some also support near-field communication (NFC) for use with a phone or tablet.
Among the many protocols supported by YubiKeys, the one which works with SSH connections to our clusters is the Yubico One-Time Password (OTP). After you have registered a YubiKey for multifactor authentication, when you log in to one of our clusters you will be prompted for a one-time password (OTP). You respond by touching a button on your YubiKey, which generates and transmits a string of 32 characters to complete your authentication.
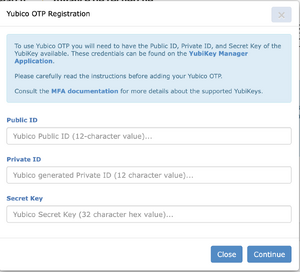
To register your YubiKey you will need its Public ID, Private ID, and Secret Key. If you have this information, go to the Multifactor authentication management page. If you do not have this information, configure your key using the steps below.
Configuring your YubiKey for Yubico OTP[edit]
- Download and install the YubiKey Manager software from the Yubico website.
- Insert your YubiKey and launch the YubiKey Manager software.
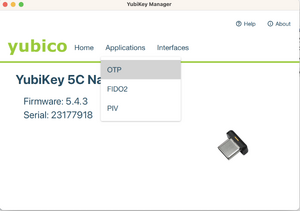
- In the YubiKey Manager software, select Applications, then OTP. (Images below illustrate this and the next few steps.)
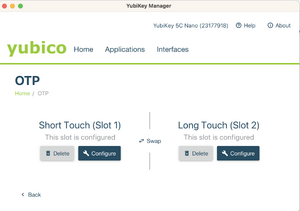
- Select Configure for either slot 1 or slot 2. Slot 1 corresponds to a short touch (pressing for 1s to 2.5), while slot 2 is a long touch on the key (pressing for 3s to 5s). Slot 1 is typically pre-registered for Yubico cloud mode. If you are already using this slot for other services, either use slot 2, or click on Swap to transfer the configuration to slot 2 before configuring slot 1.
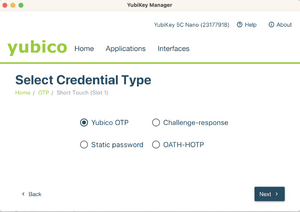
- Select Yubico OTP.
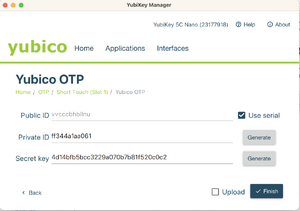
- Select Use serial, then generate a private ID and a secret key. Securely save a copy of the data in the Public ID, Private ID, and Secret Key fields before you click on Finish, as you will need the data for the next step.
- IMPORTANT: Make sure you clicked on "Finish" in the previous step.
- Log into the CCDB to register your YubiKey in the Multifactor authentication management page.
Using your second factor[edit]
When connecting via SSH[edit]
If your account has multifactor authentication enabled, when you connect via SSH to a cluster which supports MFA, you will be prompted to use your second factor after you first use either your password or your SSH key. This prompt will look like this:
[name@server ~]$ ssh cluster.computecanada.ca
Duo two-factor login for name
Enter a passcode or select one of the following options:
1. Duo Push to My phone (iOS)
Passcode or option (1-1):
At this point, you can select which phone or tablet you want Duo to send a notification to. If you have multiple devices enrolled, you will be shown a list. You will then get a notification on your device, which you accept to complete the authentication.
If you are using a YubiKey, a backup code, or if you prefer to enter the time-based one-time password that the Duo Mobile application shows, you would write these instead of selecting an option. For example:
[name@server ~]$ ssh cluster.computecanada.ca
Duo two-factor login for name
Enter a passcode or select one of the following options:
1. Duo Push to My phone (iOS)
Passcode or option (1-1):vvcccbhbllnuuebegkkbcfdftndjijlneejilrgiguki
Success. Logging you in...
Configuring your SSH client to only ask every so often[edit]
If you use OpenSSH to connect, you can reduce the frequency with which you are asked for a second factor. To do so, edit your .ssh/config to add the lines:
Host HOSTNAME
ControlPath ~/.ssh/cm-%r@%h:%p
ControlMaster auto
ControlPersist 10m
where you would replace HOSTNAME with the host name of the server for which you want this configuration.
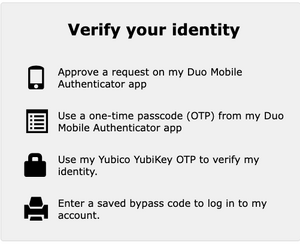
When authenticating to our account portal[edit]
Once multifactor authentication is enabled on your account, you will be required to use it when connecting to our account portal. After entering your username and password, you will see a prompt similar to this, where you click on the option you want to use.
(Note: This screen will be updated.)
Frequently asked questions[edit]
I have an Android phone which is older than Android 9. I do not find the Duo Mobile application. Can I still use Duo ?[edit]
Yes. However, you have to download the application from the Duo website. See this page for more details.
I do not have a smartphone or tablet, or they are too old. Can I still use multifactor authentication?[edit]
Yes. In this case, you need to use a YubiKey.
I have lost my second factor device. What can I do?[edit]
- If you have backup codes, or if you have more than one device, use that other mechanism to connect to your account on our account portal, and then delete your lost device from the list. Then, register a new device.
- If you do not have backup codes, or if have lost all of your devices, contact technical support for assistance.