Configuring WSL as a ControlMaster relay server: Difference between revisions
No edit summary |
(Marked this version for translation) |
||
| Line 3: | Line 3: | ||
<translate> | <translate> | ||
<!--T:1--> | |||
{{Warning|title=Disclaimer |content=This is still an experimental procedure (work in progress). Your feedback is welcome.}} | {{Warning|title=Disclaimer |content=This is still an experimental procedure (work in progress). Your feedback is welcome.}} | ||
With this procedure you can leverage ControlMaster under WSL so you may log into the clusters with several apps under native Windows for a certain period without having to do MFA for every session. | With this procedure you can leverage ControlMaster under WSL so you may log into the clusters with several apps under native Windows for a certain period without having to do MFA for every session. | ||
=== Install Linux on Windows with WSL === | === Install Linux on Windows with WSL === <!--T:2--> | ||
Please follow this link for more detailed instructions: | Please follow this link for more detailed instructions: | ||
https://docs.alliancecan.ca/wiki/Windows_Subsystem_for_Linux_(WSL) | https://docs.alliancecan.ca/wiki/Windows_Subsystem_for_Linux_(WSL) | ||
<!--T:3--> | |||
This setup assumes the following on the sample config files: | This setup assumes the following on the sample config files: | ||
* you selected Ubuntu as your distribution | * you selected Ubuntu as your distribution | ||
| Line 17: | Line 19: | ||
* the Alliance user name is <i>pinto</i> and I want to connect to Cedar | * the Alliance user name is <i>pinto</i> and I want to connect to Cedar | ||
=== Install additional packages === | === Install additional packages === <!--T:4--> | ||
<pre> | <pre> | ||
sudo apt update && sudo apt upgrade -y | sudo apt update && sudo apt upgrade -y | ||
| Line 24: | Line 26: | ||
NOTE: You may log in from Windows to Ubuntu with <code>ssh localhost</code>. | NOTE: You may log in from Windows to Ubuntu with <code>ssh localhost</code>. | ||
</pre> | </pre> | ||
=== General idea of the setup === | === General idea of the setup === <!--T:5--> | ||
<pre> | <pre> | ||
[ssh client] ----> [ssh relay server] ----> [ssh target server] | [ssh client] ----> [ssh relay server] ----> [ssh target server] | ||
| Line 32: | Line 34: | ||
</pre> | </pre> | ||
=== Log into the Ubuntu VM and create a <i>custom_ssh</i> folder === | === Log into the Ubuntu VM and create a <i>custom_ssh</i> folder === <!--T:6--> | ||
<pre> | <pre> | ||
jaime@ubuntu:~$ cat custom_ssh/sshd_config | jaime@ubuntu:~$ cat custom_ssh/sshd_config | ||
| Line 47: | Line 49: | ||
<pre>sudo cp /etc/ssh/ssh_host_ed25519_key /home/jaime/custom_ssh/</pre> | <pre>sudo cp /etc/ssh/ssh_host_ed25519_key /home/jaime/custom_ssh/</pre> | ||
=== Customize <i>.ssh/config</i> on Ubuntu === | === Customize <i>.ssh/config</i> on Ubuntu === <!--T:7--> | ||
<pre> | <pre> | ||
jaime@ubuntu:~$ cat ~/.ssh/config | jaime@ubuntu:~$ cat ~/.ssh/config | ||
| Line 58: | Line 60: | ||
</pre> | </pre> | ||
=== Customize the authorized keys === | === Customize the authorized keys === <!--T:8--> | ||
<pre> | <pre> | ||
jaime@ubuntu:~/custom_ssh$ cat /home/jaime/custom_ssh/authorized_keys | jaime@ubuntu:~/custom_ssh$ cat /home/jaime/custom_ssh/authorized_keys | ||
| Line 64: | Line 66: | ||
</pre> | </pre> | ||
<!--T:9--> | |||
NOTE: Use the same public SSH key that you uploaded to CCDB. | NOTE: Use the same public SSH key that you uploaded to CCDB. | ||
=== Now start the sshd server on Ubuntu === | === Now start the sshd server on Ubuntu === <!--T:10--> | ||
<pre> | <pre> | ||
jaime@ubuntu:~/custom_ssh$ /usr/sbin/sshd -f ${HOME}/custom_ssh/sshd_config | jaime@ubuntu:~/custom_ssh$ /usr/sbin/sshd -f ${HOME}/custom_ssh/sshd_config | ||
</pre> | </pre> | ||
<!--T:11--> | |||
NOTE: Make sure your start the server as yourself, not as root. | NOTE: Make sure your start the server as yourself, not as root. | ||
You will also need to start the sshd server every time you restart your computer, or after closing or restarting WSL. | You will also need to start the sshd server every time you restart your computer, or after closing or restarting WSL. | ||
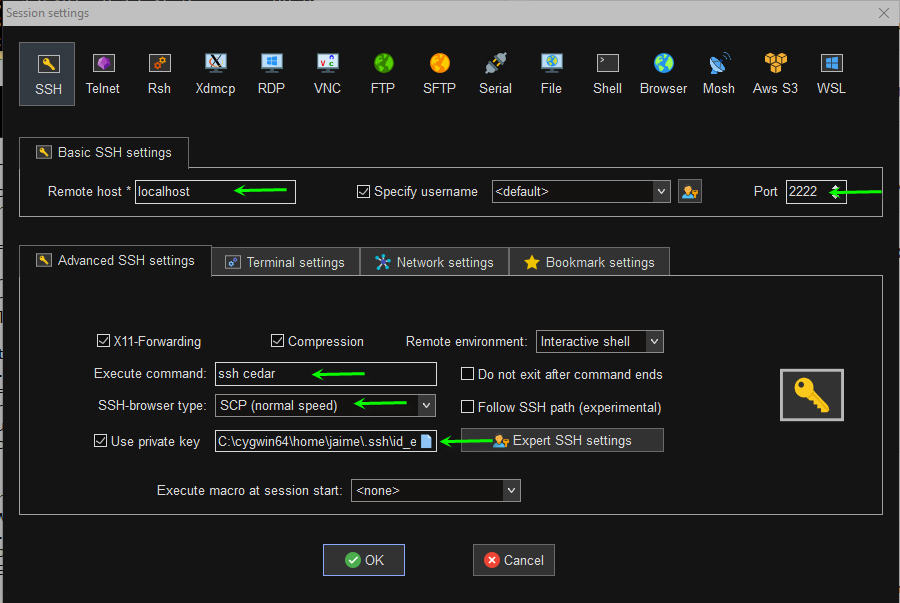
=== Customize <i>.ssh/config</i> on <i>smart</i> with <code>RemoteCommand</code> === | === Customize <i>.ssh/config</i> on <i>smart</i> with <code>RemoteCommand</code> === <!--T:12--> | ||
<pre> | <pre> | ||
jaime@smart ~/.ssh cat config | jaime@smart ~/.ssh cat config | ||
| Line 82: | Line 86: | ||
</pre> | </pre> | ||
=== You are now ready to try to log into Cedar === | === You are now ready to try to log into Cedar === <!--T:13--> | ||
<pre> | <pre> | ||
jaime@smart ~ | jaime@smart ~ | ||
| Line 96: | Line 100: | ||
</pre> | </pre> | ||
=== Alternative setup === | === Alternative setup === <!--T:14--> | ||
There is another way in which you could customize the authorized keys on Ubuntu and the <i>~/.ssh/config</i> on Windows such that it may work better for some Windows GUI apps that don't let you explicitly set the <code>RemoteCommand</code> (such as WinSCP). In this case you set the <code>RemoteCommand</code> on the public key: | There is another way in which you could customize the authorized keys on Ubuntu and the <i>~/.ssh/config</i> on Windows such that it may work better for some Windows GUI apps that don't let you explicitly set the <code>RemoteCommand</code> (such as WinSCP). In this case you set the <code>RemoteCommand</code> on the public key: | ||
<pre> | <pre> | ||
| Line 102: | Line 106: | ||
command="ssh cedar" ssh-ed25519 AAAZDINzaC1lZDI1NTE5AAC1lZDIvqzlffkzcjRAaMQoTBrPe5FxlSAjRAaMQyVzN+A+ | command="ssh cedar" ssh-ed25519 AAAZDINzaC1lZDI1NTE5AAC1lZDIvqzlffkzcjRAaMQoTBrPe5FxlSAjRAaMQyVzN+A+ | ||
<!--T:15--> | |||
jaime@smart ~/.ssh cat config | jaime@smart ~/.ssh cat config | ||
Host ubuntu | Host ubuntu | ||
| Line 108: | Line 113: | ||
</pre> | </pre> | ||
<!--T:16--> | |||
You may still <code>ssh ubuntu -p 2222</code> after that from a shell on Windows. | You may still <code>ssh ubuntu -p 2222</code> after that from a shell on Windows. | ||
=== Setup with MobaXterm === | === Setup with MobaXterm === <!--T:17--> | ||
<!--T:18--> | |||
[[File:MobaXterm-setup.jpg]] | [[File:MobaXterm-setup.jpg]] | ||
<!--T:19--> | |||
[[File:MobaXterm-VSL-localdriveC.jpg]] | [[File:MobaXterm-VSL-localdriveC.jpg]] | ||
Revision as of 19:07, 28 March 2024
This is still an experimental procedure (work in progress). Your feedback is welcome.
With this procedure you can leverage ControlMaster under WSL so you may log into the clusters with several apps under native Windows for a certain period without having to do MFA for every session.
Install Linux on Windows with WSL[edit]
Please follow this link for more detailed instructions: https://docs.alliancecan.ca/wiki/Windows_Subsystem_for_Linux_(WSL)
This setup assumes the following on the sample config files:
- you selected Ubuntu as your distribution
- the hostname for the WSL instance is ubuntu. Edit /etc/hostname (ubuntu) and /etc/hosts (127.0.0.1 localhost ubuntu)
- the Windows system is named smart and the login name is jaime
- the user name on the Ubuntu VM is also jaime
- the Alliance user name is pinto and I want to connect to Cedar
Install additional packages[edit]
sudo apt update && sudo apt upgrade -y sudo apt install openssh-server -y NOTE: You may log in from Windows to Ubuntu with <code>ssh localhost</code>.
General idea of the setup[edit]
[ssh client] ----> [ssh relay server] ----> [ssh target server] your Windows modified authorized_keys using cedar for machine in your Ubuntu VM this exercise <i>smart</i> <i>ubuntu</i> Cedar
Log into the Ubuntu VM and create a custom_ssh folder[edit]
jaime@ubuntu:~$ cat custom_ssh/sshd_config Port 2222 HostKey /home/jaime/custom_ssh/ssh_host_ed25519_key HostKey /home/jaime/custom_ssh/ssh_host_rsa_key AuthorizedKeysFile /home/jaime/custom_ssh/authorized_keys ChallengeResponseAuthentication no UsePAM no Subsystem sftp /usr/lib/openssh/sftp-server PidFile /home/jaime/custom_ssh/sshd.pid
NOTE: You may copy the ssh_host keys from /etc/ssh with:
sudo cp /etc/ssh/ssh_host_ed25519_key /home/jaime/custom_ssh/
Customize .ssh/config on Ubuntu[edit]
jaime@ubuntu:~$ cat ~/.ssh/config
Host cedar
ControlPath ~/.ssh/cm-%r@%h:%p
ControlMaster auto
ControlPersist 10m
HostName cedar.alliancecan.ca
User pinto
Customize the authorized keys[edit]
jaime@ubuntu:~/custom_ssh$ cat /home/jaime/custom_ssh/authorized_keys ssh-ed25519 AAAZDINzaC1lZDI1NTE5AAC1lZDIvqzlffkzcjRAaMQoTBrPe5FxlSAjRAaMQyVzN+A+
NOTE: Use the same public SSH key that you uploaded to CCDB.
Now start the sshd server on Ubuntu[edit]
jaime@ubuntu:~/custom_ssh$ /usr/sbin/sshd -f ${HOME}/custom_ssh/sshd_config
NOTE: Make sure your start the server as yourself, not as root. You will also need to start the sshd server every time you restart your computer, or after closing or restarting WSL.
Customize .ssh/config on smart with RemoteCommand[edit]
jaime@smart ~/.ssh cat config
Host ubuntu
Hostname localhost
RemoteCommand ssh cedar
You are now ready to try to log into Cedar[edit]
jaime@smart ~ $ ssh -t ubuntu -p 2222 Enter passphrase for key '/home/jaime/.ssh/id_ed25519': Last login: Fri Mar 22 10:50:12 2024 from 99.239.174.157 ================================================================================ Welcome to Cedar! / Bienvenue sur Cedar! ... ... ... [pinto@cedar1 ~]$
Alternative setup[edit]
There is another way in which you could customize the authorized keys on Ubuntu and the ~/.ssh/config on Windows such that it may work better for some Windows GUI apps that don't let you explicitly set the RemoteCommand (such as WinSCP). In this case you set the RemoteCommand on the public key:
jaime@ubuntu:~/custom_ssh$ cat /home/jaime/custom_ssh/authorized_keys
command="ssh cedar" ssh-ed25519 AAAZDINzaC1lZDI1NTE5AAC1lZDIvqzlffkzcjRAaMQoTBrPe5FxlSAjRAaMQyVzN+A+
jaime@smart ~/.ssh cat config
Host ubuntu
Hostname localhost
#RemoteCommand ssh cedar
You may still ssh ubuntu -p 2222 after that from a shell on Windows.
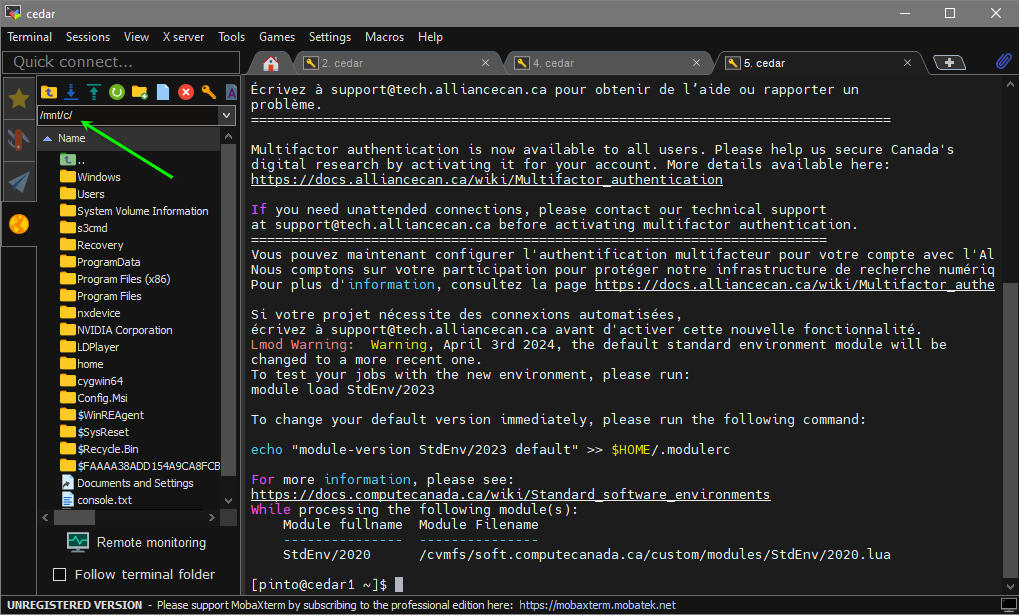
Setup with MobaXterm[edit]
Outstanding challenges[edit]
With this setup you may be prompt for MFA duo authentication only on the first session. Subsequently multiple SSH sessions can be started on Cedar without MFA. This also works fine to get remote shells on Cedar from several apps running natively on Windows. We already tried for WinSCP, but we can assume it will work for other apps with some tweaks.
However, what I'm realizing now is that on those very same Windows apps I'm not able to list/display the contents of the local Windows drives. Instead they all show the contents of the ubuntu relay server, which may not be what users want. I imagine in the most generic case they would like to transfer files directly between Windows and cedar, and not between Ubuntu and cedar. In any case, users may still see the contents of the Windows host mounted as the /mnt file system on Ubuntu as explained here.
I'm also trying to understand how to setup scp and sftp directly from Windows to cedar. To that effect, we might want explore the possibility of having a "generic command script", similar to the setup with automation under MFA, in which we could capture several commands with the pub key in the authorized_keys file.
Ultimately we can conceive multiple stanzas in the .ssh/config, one for each site (cedar, graham, beluga, ...) on different ports (2222, 2223, 2224, ...)
Therefore, I probably need a hand from some of you to figure this out. Alliance staff members could post suggestions in the security-mfa channel. Users in general please send email to support with the subject "WSL, ControlMaster/MFA suggestion". Thanks