Multifactor authentication: Difference between revisions
(reassure that we haven't broken existing automation) |
No edit summary |
||
| (122 intermediate revisions by 14 users not shown) | |||
| Line 8: | Line 8: | ||
<!--T:21--> | <!--T:21--> | ||
You can choose any of these factors for this second authentication step: | You can choose any of these factors for this second authentication step: | ||
* | *Approve a notification on a smart device through the Duo Mobile application. | ||
* | *Enter a code generated on demand. | ||
* | *Push a button on a hardware key (YubiKey). | ||
<!--T:22--> | <!--T:22--> | ||
This feature will be | This feature will be gradually deployed and will not be immediately available for all of our services. | ||
= Recorded webinars = <!--T:50--> | |||
Two webinars were presented in October 2023. Their recordings are available here: | |||
* [https://www.youtube.com/watch?v=ciycOUbchl8&ab_channel=TheAlliance%7CL%E2%80%99Alliance Authentification multifacteur pour la communauté de recherche] (French) | |||
* [https://www.youtube.com/watch?v=qNsUsZ73HP0&ab_channel=TheAlliance%7CL%E2%80%99Alliance Multifactor authentication for researchers] (English) | |||
= Registering factors = <!--T:2--> | = Registering factors = <!--T:2--> | ||
| Line 19: | Line 24: | ||
When you enable multifactor authentication for your account, we <b>strongly recommend</b> that you configure at least two options for your second factor. For example, you can use a phone and single-use codes; a phone and a hardware key; or two hardware keys. This will ensure that if you lose one factor, you can still use your other one to access your account. | When you enable multifactor authentication for your account, we <b>strongly recommend</b> that you configure at least two options for your second factor. For example, you can use a phone and single-use codes; a phone and a hardware key; or two hardware keys. This will ensure that if you lose one factor, you can still use your other one to access your account. | ||
== | == Use a smartphone or tablet == <!--T:3--> | ||
#Install the Duo Mobile authentication application from the [https://itunes.apple.com/us/app/duo-mobile/id422663827 Apple Store] or | |||
#Go to the [https://ccdb.alliancecan.ca CCDB], | <!--T:46--> | ||
#Install the Duo Mobile authentication application from the [https://itunes.apple.com/us/app/duo-mobile/id422663827 Apple Store] or [https://play.google.com/store/apps/details?id=com.duosecurity.duomobile Google Play]. Make sure to get the correct application (see icon below). TOTP applications such as Aegis, Google Authenticator, and Microsoft Authenticator are <b>not</b> compatible with Duo and will not scan the QR code. | |||
#Go to the [https://ccdb.alliancecan.ca CCDB], log in to your account and select <i>My account → [https://ccdb.alliancecan.ca/multi_factor_authentications Multifactor authentication management]</i>. | |||
#Under <i>Register a device</i>, click on <i>Duo Mobile</i>. | #Under <i>Register a device</i>, click on <i>Duo Mobile</i>. | ||
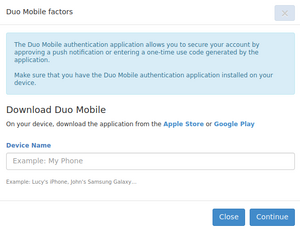
#Enter a name for your device. | #Enter a name for your device. Click on <i>Continue</i>. A QR code will be displayed. | ||
#In the Duo Mobile application, | #In the Duo Mobile application, tap <i>Set up account</i> or the “+” sign. | ||
#Tap <i>Use a QR code</i>. | |||
#Scan the QR code shown to you in CCDB. <b>Important: Make sure that your mobile device is connected to the internet (over wi-fi or cellular data) while you are scanning the QR code.</b> | |||
<gallery widths=300px heights=300px> | |||
File:Duo-mobile-app-icon.png|Step 1 | |||
File:Duo-mobile-option-en.png|Step 3 | |||
File:Naming-duo-mobile-device-en.png|Step 4 | |||
File:Duo-mobile-add-account.png|Step 5 | |||
File:Duo-mobile-scan-qr-code.png|Step 6 | |||
File:Scanning-CCDB-QR-code.jpg|Step 7 | |||
</gallery> | |||
== | == Use a YubiKey == <!--T:4--> | ||
A YubiKey is a hardware token made by the [https://www.yubico.com/ Yubico] company. If you do not have a smartphone or tablet, do not wish to use your phone or tablet for multifactor authentication, or are often in a situation when using your phone or tablet is not possible, then a YubiKey | A YubiKey is a hardware token made by the [https://www.yubico.com/ Yubico] company. If you do not have a smartphone or tablet, do not wish to use your phone or tablet for multifactor authentication, or are often in a situation when using your phone or tablet is not possible, then a YubiKey is your best option. | ||
<!--T: | <!--T:45--> | ||
<b>Note that some YubiKey models are not compatible because they don't all support the "Yubico OTP" function, which is required. We recommend using the YubiKey 5 Series, but older devices you may already have could work, see this [https://www.yubico.com/products/identifying-your-yubikey/ Yubico identification page] for reference.</b> | |||
<!--T:23--> | <!--T:23--> | ||
A YubiKey 5 is the size of a small USB stick and costs between $ | A YubiKey 5 is the size of a small USB stick and costs between $67 and $100. Different models can fit in USB-A, USB-C, or Lightning ports, and some also support near-field communication (NFC) for use with a phone or tablet. | ||
<!--T:5--> | <!--T:5--> | ||
Multiple protocols are supported by YubiKeys. Our clusters use the Yubico One-Time Password (OTP). After you have registered a YubiKey for multifactor authentication, when you log on to one of our clusters you will be prompted for a one-time password (OTP). You respond by touching a button on your YubiKey, which generates a string of 32 characters to complete your authentication. Using a YubiKey does not require any typing on the keyboard: the YubiKey connected to your computer “types” the 32-character string when you touch its button. | |||
<!--T:6--> | <!--T:6--> | ||
To register your YubiKey you will need its Public ID, Private ID, and Secret Key. | To register your YubiKey you will need its Public ID, Private ID, and Secret Key. If you have this information, go to the [https://ccdb.computecanada.ca/multi_factor_authentications Multifactor authentication management page]. If you do not have this information, configure your key using the steps below. | ||
=== Configuring your YubiKey for Yubico OTP === <!--T:7--> | === Configuring your YubiKey for Yubico OTP === <!--T:7--> | ||
| Line 47: | Line 64: | ||
# Insert your YubiKey and launch the YubiKey Manager software. | # Insert your YubiKey and launch the YubiKey Manager software. | ||
# In the YubiKey Manager software, select <i>Applications</i>, then <i>OTP</i>. (Images below illustrate this and the next few steps.) | # In the YubiKey Manager software, select <i>Applications</i>, then <i>OTP</i>. (Images below illustrate this and the next few steps.) | ||
# Select <i>Configure</i> for either slot 1 or slot 2. Slot 1 corresponds to a short touch (pressing for | # Select <i>Configure</i> for either slot 1 or slot 2. Slot 1 corresponds to a short touch (pressing for 1 to 2.5 seconds), while slot 2 is a long touch on the key (pressing for 3 to 5 seconds). Slot 1 is typically pre-registered for Yubico cloud mode. If you are already using this slot for other services, either use slot 2, or click on <i>Swap</i> to transfer the configuration to slot 2 before configuring slot 1. | ||
# Select <i>Yubico OTP</i>. | # Select <i>Yubico OTP</i>. | ||
# Select <i>Use serial</i>, then generate a private ID and a secret key. <b>Securely save a copy of the data in the Public ID, Private ID, and Secret Key fields before you click on <i>Finish</i>, as you will need the data for the next step.</b> | # Select <i>Use serial</i>, then generate a private ID and a secret key. <b>Securely save a copy of the data in the Public ID, Private ID, and Secret Key fields before you click on <i>Finish</i>, as you will need the data for the next step.</b> | ||
| Line 59: | Line 76: | ||
CCDB Yubikeys.png|Step 8 | CCDB Yubikeys.png|Step 8 | ||
</gallery> | </gallery> | ||
<!--T:93--> | |||
You can test your Yubikey setup by pressing the button on it any time while it is inserted into your computer. If set up correctly, it should generate a code at your prompt or cursor. | |||
= Using your second factor = <!--T:9--> | = Using your second factor = <!--T:9--> | ||
== When connecting via SSH == | == When connecting via SSH == | ||
When you connect to a cluster using SSH, you will be prompted for your second factor after you first supply either your password or your [[SSH Keys|SSH key]]. This prompt will look like this: | |||
{{Command|ssh cluster.computecanada.ca | {{Command|ssh cluster.computecanada.ca | ||
|result= Duo two-factor login for name | |result= Duo two-factor login for name | ||
| Line 77: | Line 97: | ||
<!--T:13--> | <!--T:13--> | ||
If you are using a YubiKey, a backup code | If you are using a YubiKey, simply touch the YubiKey when the "Passcode" prompt appears. | ||
If you are using a backup code or a time-based one-time password that the Duo Mobile application shows, you will have to paste it or type it at the prompt. | |||
{{Command|ssh cluster.computecanada.ca | {{Command|ssh cluster.computecanada.ca | ||
|result= Duo two-factor login for name | |result= Duo two-factor login for name | ||
| Line 91: | Line 112: | ||
Success. Logging you in...}} | Success. Logging you in...}} | ||
=== Configuring your SSH client | === Configuring your SSH client with ControlMaster === <!--T:17--> | ||
If you use OpenSSH to connect, you can reduce | |||
==== Linux and MacOS ==== <!--T:18--> | |||
If you use OpenSSH to connect, you can reduce how frequently you are asked for a second factor. To do so, edit your <code>.ssh/config</code> to add the lines: | |||
<!--T:24--> | <!--T:24--> | ||
| Line 101: | Line 124: | ||
ControlPersist 10m | ControlPersist 10m | ||
</pre> | </pre> | ||
where you would replace <code>HOSTNAME</code> with the host name of the server for which you want this configuration. | where you would replace <code>HOSTNAME</code> with the host name of the server for which you want this configuration. This setting allows a first SSH session to ask for the first and second factors, but subsequent SSH connections on the same device will reuse the connection of the first session (without asking for authentication), even up to 10 minutes after that first session was disconnected. | ||
<!--T:41--> | <!--T:41--> | ||
Note that the above ControlMaster mechanism (a.k.a. Multiplexing) doesn't work with native Windows, in which case [https://learn.microsoft.com/en-gb/windows/wsl/about Windows Subsystem for Linux] will be required. [https://docs.alliancecan.ca/wiki/Configuring_WSL_as_a_ControlMaster_relay_server See the link below]. | |||
====Windows ==== <!--T:67--> | |||
<!--T:89--> | |||
See [[Configuring WSL as a ControlMaster relay server]]. | |||
== When authenticating to our account portal == <!--T: | == When authenticating to our account portal == <!--T:88--> | ||
Once multifactor authentication is enabled on your account, you will be required to use it when connecting to our account portal. After entering your username and password, you will see a prompt similar to this, where you click on the option you want to use. <br> | Once multifactor authentication is enabled on your account, you will be required to use it when connecting to our account portal. After entering your username and password, you will see a prompt similar to this, where you click on the option you want to use. <br> | ||
(Note: <i>This screen will be updated</i>.) | (Note: <i>This screen will be updated</i>.) | ||
| Line 114: | Line 142: | ||
= Configuring common SSH clients = <!--T:32--> | = Configuring common SSH clients = <!--T:32--> | ||
Command line clients will typically support multifactor authentication without additional configuration. This is however often not the case for graphical clients. Below are instructions | Command line clients will typically support multifactor authentication without additional configuration. This is however often not the case for graphical clients. Below are instructions specific to a few of them. | ||
== FileZilla == <!--T:33--> | == FileZilla == <!--T:33--> | ||
| Line 135: | Line 163: | ||
# Select “OK” to save the connection | # Select “OK” to save the connection | ||
# Test the connection | # Test the connection | ||
=== Niagara special case === <!--T:59--> | |||
Connections in FileZilla can only be configured to use either SSH keys or interactive prompts, not both. Since Niagara requires using SSH keys and an MFA prompt, using FileZilla is challenging. We recommend using a different SCP client that has better support for interactive prompt, but one possible way to work around is to: | |||
<!--T:60--> | |||
# Attempt to connect with an SSH key. This will fail because of the interactive prompt for the second factor. FileZilla will then remember your key. | |||
# Change the login method to interactive and attempt to connect again. You will then receive the 2FA prompt. | |||
== MobaXTerm == <!--T:36--> | == MobaXTerm == <!--T:36--> | ||
Install version 23.1 or more | Install version 23.1 or later. | ||
[https://web.archive.org/web/20231214123606/mobaxterm.mobatek.net/download-home-edition.html Version 23.5] (on Archive.org) is the latest version for which the following instructions work for most users. | |||
==== Prompt on file transfer ==== <!--T:69--> | |||
<!--T:43--> | |||
When connecting to a remote server, MobaXterm establishes two connections by default: | |||
the first for the terminal and the second for the remote file browser. | |||
By default, the file browser uses the <i>SFTP protocol</i>, | |||
which causes a mandatory second prompt for your second factor of authentication. | |||
<!--T:66--> | |||
This behaviour can be improved by switching the <i>SSH-browser type</i> to | |||
"SCP (enhanced speed)" or "SCP (normal speed)" in the session's <i>Advanced SSH settings</i>. | |||
==== Use SSH key instead of password ==== <!--T:70--> | |||
<!--T:71--> | |||
To resolve the following issues (1) allow downloads and (2) use SSH passphrase instead of Digital Research Alliance of Canada password, make the following changes to SSH settings (SSH tab in Settings dialogue): | |||
<!--T:72--> | |||
<ol> | |||
<li>Uncheck "GSSAPI Kerberos"</li> | |||
<li>Uncheck "Use external Pageant"</li> | |||
<li>Check "Use internal SSH agent "MobAgent""</li> | |||
<li>Use the "+" button to select SSH key file.</li> | |||
</ol> | |||
<!-- | |||
First image shows the default SSH settings and the second image shows the changes described above: | |||
[[File:Ssh Settings Default|thumb|Default SSH Settings]] | |||
[[File:Ssh Settings Changes|thumb|Changes to correct download and login issue]] | |||
--> | |||
==== Known issues with MFA ==== <!--T:90--> | |||
We noticed that after adoption of MFA, MobaXTerm presents a strange behavior, more or less prevalent depending on the version. Although files can be opened via the terminal, when you try to open, download, or upload files using the navigation bar on the left, operations hang indefinitely. | |||
<!--T:91--> | |||
Basically there are pretty much 3 independent sessions that need to be initiated and authenticated when you use MobaXterm: | |||
<ol> | |||
<li>to open the ssh terminal | |||
<li>to display the contents of the folder on the left pane | |||
<li>to start the transfer of files | |||
</ol> | |||
It's possible that 1 or 2 hidden MFA-Duo windows (behind other windows) on your computer are waiting for authentication. | |||
<!--T:92--> | |||
In addition, each time you navigate to a different folder on the left pane, another transaction requiring MFA is started. Some versions of MobaXterm handle this better than others. | |||
== PuTTY == <!--T:37--> | == PuTTY == <!--T:37--> | ||
Install version 0.72 or | Install version 0.72 or later. | ||
== WinSCP == <!--T:38--> | == WinSCP == <!--T:38--> | ||
| Line 146: | Line 227: | ||
== PyCharm == <!--T:39--> | == PyCharm == <!--T:39--> | ||
In order to connect to our clusters with PyCharm, you must setup your [[SSH Keys]] before connecting. | |||
<!--T:65--> | |||
When you connect to a remote host in PyCharm, enter your username and the host you want to connect to. You will then be asked to enter a "One time password" during the authentication process. At this stage, use either your YubiKey or your generated password in Duo, depending on what you have setup in your account. | |||
== Cyberduck == <!--T:47--> | |||
By default, Cyberduck opens a new connection for every file transfer, prompting you for your second factor each time. To change this, go in the application's preferences, under <i>Transfers</i>, in the <i>General</i> section, use the drop-down menu beside the <i>Transfer Files</i> item and select <i>Use browser connection</i>. | |||
<!--T:48--> | |||
Then, ensure that the box beside <i>Segmented downloads with multiple connections per file</i> is not checked. It should look like the picture below. | |||
<!--T:49--> | |||
[[File:CyberDuck configuration for multifactor authentication.png|400px|Cyberduck configuration for multifactor authentication]] | |||
= Frequently asked questions = <!--T:19--> | = Frequently asked questions = <!--T:19--> | ||
== I have | == Can I use Authy/Google authenticator/Microsoft Authenticator ? == | ||
Yes. However, you have to download the application from the Duo website. | No. Only Duo Mobile will work. | ||
== I do not have a smartphone or tablet, and I do not want to buy a Yubikey == <!--T:55--> | |||
Unfortunately, that means you will not be able to use our services when multifactor authentication becomes mandatory. A Yubikey hardware | |||
token is the cheapest way to enable multifactor authentication on your account, and is expected to be covered by the principal investigator's | |||
research funding like any other work-related hardware. Mandating multifactor authentication is a requirement from our funding bodies. | |||
== Why can't you send me one time passcodes through SMS ? == <!--T:56--> | |||
Sending SMS costs money which we do not have. Multifactor using SMS is also widely regarded as insecure by most security experts. | |||
== Why can't you send me one time passcodes through email ? == <!--T:57--> | |||
No, Duo does not support sending one time code through email. | |||
== I have an older Android phone and I cannot download the Duo Mobile application from the Google Play site. Can I still use Duo ? == <!--T:58--> | |||
Yes. However, you have to download the application from the Duo website: | |||
<!--T:52--> | |||
* For Android 8 and 9, the latest compatible version is [https://dl.duosecurity.com/DuoMobile-4.33.0.apk DuoMobile-4.33.0.apk] | |||
* For Android 10, the latest compatible version is [https://dl.duosecurity.com/DuoMobile-4.56.0.apk DuoMobile-4.56.0.apk] | |||
<!--T:53--> | |||
For validation, official [https://duo.com/docs/checksums#duo-mobile SHA-256 checksums are listed here]. | |||
<!--T:54--> | |||
For installation instructions, [https://help.duo.com/s/article/2211?language=en_US see this page]. | |||
== I want to disable multifactor authentication. How do I do this? == <!--T:51--> | |||
Multifactor authentication is mandatory. Users cannot disable it. Exceptions can only be granted for automation purposes. If you find that multifactor authentication is annoying, we recommend applying one of the configurations listed above, depending on the SSH client you are using. Our [[Multifactor_authentication#Recorded_webinars|recorded webinars]] also contain many tips on how to make MFA less burdensome to use. | |||
== I do not have a smartphone or tablet, or they are too old. Can I still use multifactor authentication? == <!--T:25--> | == I do not have a smartphone or tablet, or they are too old. Can I still use multifactor authentication? == <!--T:25--> | ||
Yes. In this case, you need [[# | Yes. In this case, you need [[#Use a YubiKey|to use a YubiKey]]. | ||
== I have lost my second factor device. What can I do? == <!--T:20--> | == I have lost my second factor device. What can I do? == <!--T:20--> | ||
| Line 159: | Line 279: | ||
* If you do not have backup codes or have lost all of your devices, copy the following list providing answers to as many questions as you can. Email this information to support@tech.alliancecan.ca. | * If you do not have backup codes or have lost all of your devices, copy the following list providing answers to as many questions as you can. Email this information to support@tech.alliancecan.ca. | ||
<!--T:30--> | |||
What is the primary email address registered in your account? | What is the primary email address registered in your account? | ||
For how long have you had an active account with us? | For how long have you had an active account with us? | ||
What is your research area? | What is your research area? | ||
| Line 175: | Line 295: | ||
== Which SSH clients can be used when multifactor authentication is configured? == <!--T:29--> | == Which SSH clients can be used when multifactor authentication is configured? == <!--T:29--> | ||
* Most clients that use a command-line interface, such as on Linux and Mac OS. | * Most clients that use a command-line interface, such as on Linux and Mac OS. | ||
* MobaXTerm | * [[#Cyberduck|Cyberduck]] | ||
* PuTTY | * [[#FileZilla|FileZilla]] | ||
* JuiceSSH on Android | |||
* [[#MobaXTerm|MobaXTerm]] | |||
* [[#PuTTY|PuTTY]] | |||
* [[#PyCharm|PyCharm]] | |||
* Termius on iOS | * Termius on iOS | ||
* VSCode | * VSCode | ||
* [[#WinSCP|WinSCP]] | |||
== I need to have automated connections to the clusters through my account. Can I use multifactor authentication ? == <!--T:31--> | == I need to have automated SSH connections to the clusters through my account. Can I use multifactor authentication ? == <!--T:31--> | ||
We are currently deploying a set of login nodes dedicated to automated processes that require unattended SSH connections. More information about this can be found [[Automation_in_the_context_of_multifactor_authentication|here]]. | |||
== Why have I received the message "Access denied. Duo Security does not provide services in your current location" ? == <!--T:44--> | |||
Duo blocks authentications from users whose IP address originates in a country or a region subject to economic and trade sanctions: [https://help.duo.com/s/article/7544?language=en_US Duo help]. | |||
= Advanced usage = <!--T:27--> | = Advanced usage = <!--T:27--> | ||
Latest revision as of 20:05, 1 October 2024
Multifactor authentication (MFA) allows you to protect your account with more than a password. Once your account is configured to use this feature, you will need to enter your username and password as usual, and then perform a second action (the second factor) to access most of our services.
You can choose any of these factors for this second authentication step:
- Approve a notification on a smart device through the Duo Mobile application.
- Enter a code generated on demand.
- Push a button on a hardware key (YubiKey).
This feature will be gradually deployed and will not be immediately available for all of our services.
Recorded webinars[edit]
Two webinars were presented in October 2023. Their recordings are available here:
- Authentification multifacteur pour la communauté de recherche (French)
- Multifactor authentication for researchers (English)
Registering factors[edit]
Registering multiple factors[edit]
When you enable multifactor authentication for your account, we strongly recommend that you configure at least two options for your second factor. For example, you can use a phone and single-use codes; a phone and a hardware key; or two hardware keys. This will ensure that if you lose one factor, you can still use your other one to access your account.
Use a smartphone or tablet[edit]
- Install the Duo Mobile authentication application from the Apple Store or Google Play. Make sure to get the correct application (see icon below). TOTP applications such as Aegis, Google Authenticator, and Microsoft Authenticator are not compatible with Duo and will not scan the QR code.
- Go to the CCDB, log in to your account and select My account → Multifactor authentication management.
- Under Register a device, click on Duo Mobile.
- Enter a name for your device. Click on Continue. A QR code will be displayed.
- In the Duo Mobile application, tap Set up account or the “+” sign.
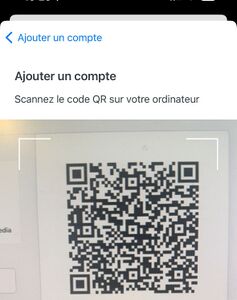
- Tap Use a QR code.
- Scan the QR code shown to you in CCDB. Important: Make sure that your mobile device is connected to the internet (over wi-fi or cellular data) while you are scanning the QR code.
Use a YubiKey[edit]
A YubiKey is a hardware token made by the Yubico company. If you do not have a smartphone or tablet, do not wish to use your phone or tablet for multifactor authentication, or are often in a situation when using your phone or tablet is not possible, then a YubiKey is your best option.
Note that some YubiKey models are not compatible because they don't all support the "Yubico OTP" function, which is required. We recommend using the YubiKey 5 Series, but older devices you may already have could work, see this Yubico identification page for reference.
A YubiKey 5 is the size of a small USB stick and costs between $67 and $100. Different models can fit in USB-A, USB-C, or Lightning ports, and some also support near-field communication (NFC) for use with a phone or tablet.
Multiple protocols are supported by YubiKeys. Our clusters use the Yubico One-Time Password (OTP). After you have registered a YubiKey for multifactor authentication, when you log on to one of our clusters you will be prompted for a one-time password (OTP). You respond by touching a button on your YubiKey, which generates a string of 32 characters to complete your authentication. Using a YubiKey does not require any typing on the keyboard: the YubiKey connected to your computer “types” the 32-character string when you touch its button.
To register your YubiKey you will need its Public ID, Private ID, and Secret Key. If you have this information, go to the Multifactor authentication management page. If you do not have this information, configure your key using the steps below.
Configuring your YubiKey for Yubico OTP[edit]
- Download and install the YubiKey Manager software from the Yubico website.
- Insert your YubiKey and launch the YubiKey Manager software.
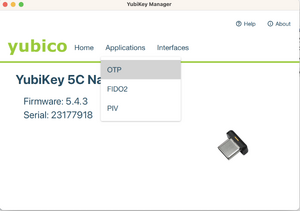
- In the YubiKey Manager software, select Applications, then OTP. (Images below illustrate this and the next few steps.)
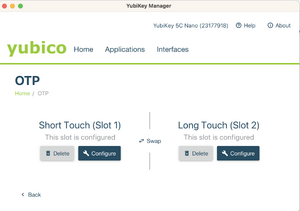
- Select Configure for either slot 1 or slot 2. Slot 1 corresponds to a short touch (pressing for 1 to 2.5 seconds), while slot 2 is a long touch on the key (pressing for 3 to 5 seconds). Slot 1 is typically pre-registered for Yubico cloud mode. If you are already using this slot for other services, either use slot 2, or click on Swap to transfer the configuration to slot 2 before configuring slot 1.
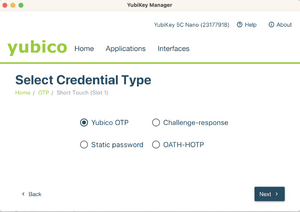
- Select Yubico OTP.
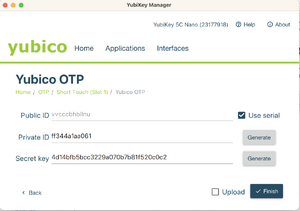
- Select Use serial, then generate a private ID and a secret key. Securely save a copy of the data in the Public ID, Private ID, and Secret Key fields before you click on Finish, as you will need the data for the next step.
- IMPORTANT: Make sure you clicked on "Finish" in the previous step.
- Log into the CCDB to register your YubiKey in the Multifactor authentication management page.
You can test your Yubikey setup by pressing the button on it any time while it is inserted into your computer. If set up correctly, it should generate a code at your prompt or cursor.
Using your second factor[edit]
When connecting via SSH[edit]
When you connect to a cluster using SSH, you will be prompted for your second factor after you first supply either your password or your SSH key. This prompt will look like this:
[name@server ~]$ ssh cluster.computecanada.ca
Duo two-factor login for name
Enter a passcode or select one of the following options:
1. Duo Push to My phone (iOS)
Passcode or option (1-1):
At this point, you can select which phone or tablet you want Duo to send a notification to. If you have multiple devices enrolled, you will be shown a list. You will then get a notification on your device, which you accept to complete the authentication.
If you are using a YubiKey, simply touch the YubiKey when the "Passcode" prompt appears. If you are using a backup code or a time-based one-time password that the Duo Mobile application shows, you will have to paste it or type it at the prompt.
[name@server ~]$ ssh cluster.computecanada.ca
Duo two-factor login for name
Enter a passcode or select one of the following options:
1. Duo Push to My phone (iOS)
Passcode or option (1-1):vvcccbhbllnuuebegkkbcfdftndjijlneejilrgiguki
Success. Logging you in...
Configuring your SSH client with ControlMaster[edit]
Linux and MacOS[edit]
If you use OpenSSH to connect, you can reduce how frequently you are asked for a second factor. To do so, edit your .ssh/config to add the lines:
Host HOSTNAME
ControlPath ~/.ssh/cm-%r@%h:%p
ControlMaster auto
ControlPersist 10m
where you would replace HOSTNAME with the host name of the server for which you want this configuration. This setting allows a first SSH session to ask for the first and second factors, but subsequent SSH connections on the same device will reuse the connection of the first session (without asking for authentication), even up to 10 minutes after that first session was disconnected.
Note that the above ControlMaster mechanism (a.k.a. Multiplexing) doesn't work with native Windows, in which case Windows Subsystem for Linux will be required. See the link below.
Windows[edit]
See Configuring WSL as a ControlMaster relay server.
When authenticating to our account portal[edit]
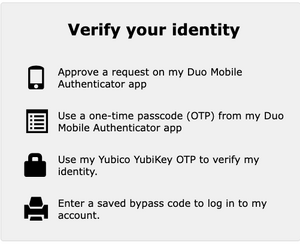
Once multifactor authentication is enabled on your account, you will be required to use it when connecting to our account portal. After entering your username and password, you will see a prompt similar to this, where you click on the option you want to use.
(Note: This screen will be updated.)
Configuring common SSH clients[edit]
Command line clients will typically support multifactor authentication without additional configuration. This is however often not the case for graphical clients. Below are instructions specific to a few of them.
FileZilla[edit]
FileZilla will ask the password and second factor each time a transfer is initiated because by default, transfers use independent connections which are closed automatically after some idle time.
To avoid entering the password and second factor multiple times, you can limit the number of connections to each site to “1” in “Site Manager” => “Transfer Settings tab”; note that you’ll then lose the ability to browse the server during transfers.
- Launch FileZilla and select “Site Manager”
- From the “Site Manager”, create a new site (or edit an existing one)
- On the “General” tab, specify the following:
- Protocol: “SFTP – SSH File Transfer Protocol”
- Host: [the cluster login hostname]
- Logon Type: “Interactive”
- User: [your username]
- On the “Transfer Settings” tab, specify the following:
- Limit number of simultaneous connections: [checked]
- Maximum number of connections: 1
- Select “OK” to save the connection
- Test the connection
Niagara special case[edit]
Connections in FileZilla can only be configured to use either SSH keys or interactive prompts, not both. Since Niagara requires using SSH keys and an MFA prompt, using FileZilla is challenging. We recommend using a different SCP client that has better support for interactive prompt, but one possible way to work around is to:
- Attempt to connect with an SSH key. This will fail because of the interactive prompt for the second factor. FileZilla will then remember your key.
- Change the login method to interactive and attempt to connect again. You will then receive the 2FA prompt.
MobaXTerm[edit]
Install version 23.1 or later. Version 23.5 (on Archive.org) is the latest version for which the following instructions work for most users.
Prompt on file transfer[edit]
When connecting to a remote server, MobaXterm establishes two connections by default: the first for the terminal and the second for the remote file browser. By default, the file browser uses the SFTP protocol, which causes a mandatory second prompt for your second factor of authentication.
This behaviour can be improved by switching the SSH-browser type to "SCP (enhanced speed)" or "SCP (normal speed)" in the session's Advanced SSH settings.
Use SSH key instead of password[edit]
To resolve the following issues (1) allow downloads and (2) use SSH passphrase instead of Digital Research Alliance of Canada password, make the following changes to SSH settings (SSH tab in Settings dialogue):
- Uncheck "GSSAPI Kerberos"
- Uncheck "Use external Pageant"
- Check "Use internal SSH agent "MobAgent""
- Use the "+" button to select SSH key file.
Known issues with MFA[edit]
We noticed that after adoption of MFA, MobaXTerm presents a strange behavior, more or less prevalent depending on the version. Although files can be opened via the terminal, when you try to open, download, or upload files using the navigation bar on the left, operations hang indefinitely.
Basically there are pretty much 3 independent sessions that need to be initiated and authenticated when you use MobaXterm:
- to open the ssh terminal
- to display the contents of the folder on the left pane
- to start the transfer of files
It's possible that 1 or 2 hidden MFA-Duo windows (behind other windows) on your computer are waiting for authentication.
In addition, each time you navigate to a different folder on the left pane, another transaction requiring MFA is started. Some versions of MobaXterm handle this better than others.
PuTTY[edit]
Install version 0.72 or later.
WinSCP[edit]
Ensure that you are using SSH Keys.
PyCharm[edit]
In order to connect to our clusters with PyCharm, you must setup your SSH Keys before connecting.
When you connect to a remote host in PyCharm, enter your username and the host you want to connect to. You will then be asked to enter a "One time password" during the authentication process. At this stage, use either your YubiKey or your generated password in Duo, depending on what you have setup in your account.
Cyberduck[edit]
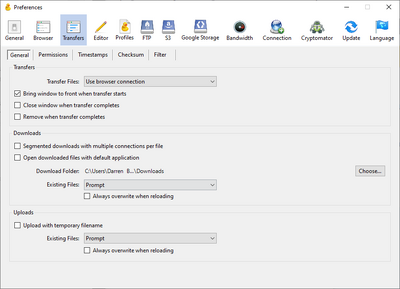
By default, Cyberduck opens a new connection for every file transfer, prompting you for your second factor each time. To change this, go in the application's preferences, under Transfers, in the General section, use the drop-down menu beside the Transfer Files item and select Use browser connection.
Then, ensure that the box beside Segmented downloads with multiple connections per file is not checked. It should look like the picture below.
Frequently asked questions[edit]
Can I use Authy/Google authenticator/Microsoft Authenticator ?[edit]
No. Only Duo Mobile will work.
I do not have a smartphone or tablet, and I do not want to buy a Yubikey[edit]
Unfortunately, that means you will not be able to use our services when multifactor authentication becomes mandatory. A Yubikey hardware token is the cheapest way to enable multifactor authentication on your account, and is expected to be covered by the principal investigator's research funding like any other work-related hardware. Mandating multifactor authentication is a requirement from our funding bodies.
Why can't you send me one time passcodes through SMS ?[edit]
Sending SMS costs money which we do not have. Multifactor using SMS is also widely regarded as insecure by most security experts.
Why can't you send me one time passcodes through email ?[edit]
No, Duo does not support sending one time code through email.
I have an older Android phone and I cannot download the Duo Mobile application from the Google Play site. Can I still use Duo ?[edit]
Yes. However, you have to download the application from the Duo website:
- For Android 8 and 9, the latest compatible version is DuoMobile-4.33.0.apk
- For Android 10, the latest compatible version is DuoMobile-4.56.0.apk
For validation, official SHA-256 checksums are listed here.
For installation instructions, see this page.
I want to disable multifactor authentication. How do I do this?[edit]
Multifactor authentication is mandatory. Users cannot disable it. Exceptions can only be granted for automation purposes. If you find that multifactor authentication is annoying, we recommend applying one of the configurations listed above, depending on the SSH client you are using. Our recorded webinars also contain many tips on how to make MFA less burdensome to use.
I do not have a smartphone or tablet, or they are too old. Can I still use multifactor authentication?[edit]
Yes. In this case, you need to use a YubiKey.
I have lost my second factor device. What can I do?[edit]
- If you have backup codes, or if you have more than one device, use that other mechanism to connect to your account on our account portal, and then delete your lost device from the list. Then, register a new device.
- If you do not have backup codes or have lost all of your devices, copy the following list providing answers to as many questions as you can. Email this information to support@tech.alliancecan.ca.
What is the primary email address registered in your account? For how long have you had an active account with us? What is your research area? What is your IP address? (to see your IP address, point your browser to this link). Who is the principal investigator sponsoring your account? Who are your group members? Who can we contact to validate your request? Which clusters do you use the most? Which modules do you load most often? When did you run your last job? Provide a few of your latest job IDs. Provide ticket topics and ticket IDs from your recent requests for technical support.
Which SSH clients can be used when multifactor authentication is configured?[edit]
- Most clients that use a command-line interface, such as on Linux and Mac OS.
- Cyberduck
- FileZilla
- JuiceSSH on Android
- MobaXTerm
- PuTTY
- PyCharm
- Termius on iOS
- VSCode
- WinSCP
I need to have automated SSH connections to the clusters through my account. Can I use multifactor authentication ?[edit]
We are currently deploying a set of login nodes dedicated to automated processes that require unattended SSH connections. More information about this can be found here.
Why have I received the message "Access denied. Duo Security does not provide services in your current location" ?[edit]
Duo blocks authentications from users whose IP address originates in a country or a region subject to economic and trade sanctions: Duo help.
Advanced usage[edit]
Configuring your YubiKey for Yubico OTP using the Command Line (ykman)[edit]
- Install the command line YubiKey Manager software (
ykman) following instructions for your OS from Yubico's ykman guide. - Insert your YubiKey and read key information with the command
ykman info. - Read OTP information with the command
ykman otp info. - Select the slot you wish to program and use the command
ykman otp yubiotpto program it. - Securely save a copy of the data in the Public ID, Private ID, and Secret Key fields. You will need the data for the next step.
- Log into the CCDB to register your YubiKey in the Multifactor authentication management page.
[name@yourLaptop]$ ykman otp yubiotp -uGgP vvcccctffclk 2 Using a randomly generated private ID: bc3dd98eaa12 Using a randomly generated secret key: ae012f11bc5a00d3cac00f1d57aa0b12 Upload credential to YubiCloud? [y/N]: y Upload to YubiCloud initiated successfully. Program an OTP credential in slot 2? [y/N]: y Opening upload form in browser: https://upload.yubico.com/proceed/4567ad02-c3a2-1234-a1c3-abe3f4d21c69