Sharing data: Difference between revisions
No edit summary |
No edit summary Tag: Manual revert |
||
| (35 intermediate revisions by 8 users not shown) | |||
| Line 3: | Line 3: | ||
<translate> | <translate> | ||
<!--T:24--> | <!--T:24--> | ||
<i>Parent page: [[Storage and file management]]</i> | |||
<!--T:49--> | |||
<b>IMPORTANT NOTE: Don't ever issue a bulk <code>chmod -R 777</code> on your home folder, in fact on any of your folders for that matter. This is a HUGE security risk, and is completely unacceptable on shared facilities such as our clusters. In addition, it's never necessary.</b> | |||
<!--T:9--> | <!--T:9--> | ||
Having to share some but not all of your data with a colleague or another research group is a common occurrence. | Having to share some but not all of your data with a colleague or another research group is a common occurrence. Our systems provide a variety of mechanisms to facilitate this data sharing with colleagues. If the person you want to share the data with is a member of the same research group as you, then the best approach may be to make use of the [[Project_layout | project space]] that each research group has in common; if your research requires the creation of a group on one of the national clusters, you can request this by contacting [[Technical support|technical support]] since users cannot create their own groups. At the opposite extreme, if the person you need to share the data with doesn't even have an account on the cluster, you can use [[Globus]] and in particular what is called a [[Globus#Globus_Sharing | shared endpoint]] to share the data. To handle the scenario of sharing with a colleague who has an account on the cluster but doesn't belong to a common research group with you, the simplest approach is to use the permissions available in the filesystem to share the data, the principal topic of this page. | ||
<!--T:12--> | <!--T:12--> | ||
When sharing a file it's important to realize that the individual you want to share it with must have access to the entire chain of directories leading from <code>/scratch</code> or <code>/project</code> to the directory in which the file is located. If we consider the metaphor of a document locked in a safe in the bedroom of your apartment in a large building, giving me the combination to the safe will not allow me to read this document if I do not also have the necessary keys to enter the apartment building, your apartment and finally your bedroom. In the context of a filesystem, this means having execute permission for each directory between the root (e.g. <code>/scratch</code> or <code>/project</code>) and the directory containing the file. | When sharing a file, it's important to realize that the individual you want to share it with must have access to the entire chain of directories leading from <code>/scratch</code> or <code>/project</code> to the directory in which the file is located. If we consider the metaphor of a document locked in a safe in the bedroom of your apartment in a large building, giving me the combination to the safe will not allow me to read this document if I do not also have the necessary keys to enter the apartment building, your apartment and finally your bedroom. In the context of a filesystem, this means having execute permission for each directory between the root (e.g. <code>/scratch</code> or <code>/project</code>) and the directory containing the file. | ||
==Filesystem permissions== <!--T:1--> | ==Filesystem permissions== <!--T:1--> | ||
<!--T:2--> | <!--T:2--> | ||
Like most modern filesystems, those used on | Like most modern filesystems, those used on our clusters support the idea of permissions to read, write, and execute files and directories. When you attempt to read, modify or delete a file, or access a directory, e.g. with <code>cd</code>, the Linux kernel first verifies that you have the right to do this. If not, you'll see the error message <i>Permission denied</i>. For each filesystem object (file or directory) there are three categories of users: | ||
* the object's owner --- normally the user who created the object, | * the object's owner --- normally the user who created the object, | ||
* members of the object's group --- normally the same as the owner's default group, and | * members of the object's group --- normally the same as the owner's default group, and | ||
| Line 23: | Line 26: | ||
You can see what the current permissions are for a filesystem object with the command | You can see what the current permissions are for a filesystem object with the command | ||
{{Command|ls -l name_of_object}} | {{Command|ls -l name_of_object}} | ||
which will print out the permissions for the owner, the group, and everyone else. For example, a file with permissions < | which will print out the permissions for the owner, the group, and everyone else. For example, a file with permissions <code>‑rw‑r‑‑r‑‑</code> means the owner can read it and write it but not execute it, and the group members and everyone else can only read the file. You'll also see printed out the name of the object's owner and the group. | ||
<!--T:4--> | <!--T:4--> | ||
To change the permissions of a file or directory you can use the command < | To change the permissions of a file or directory you can use the command <code>chmod</code> along with the user category, a plus or minus sign indicating that permission is granted or withdrawn, and the nature of the permission: read (<code>r</code>), write (<code>w</code>) or execute (<code>x</code>). For the user category, we use the abbreviations <code>u</code> for the owner (user), <code>g</code> for the group and <code>o</code> for others, i.e. everyone else on the cluster. So a command like | ||
{{Command|chmod g+r file.txt}} | {{Command|chmod g+r file.txt}} | ||
would grant read permission to all members of the group that file.txt belongs to, while | would grant read permission to all members of the group that file.txt belongs to, while | ||
{{Command|chmod o-x script.py}} | {{Command|chmod o-x script.py}} | ||
would withdraw execute permission for the file script.py to everyone but the owner and the group. We can also use the user category < | would withdraw execute permission for the file script.py to everyone but the owner and the group. We can also use the user category <code>a</code> to denote everyone (all), thus | ||
{{Command|chmod a+r file.txt}} | {{Command|chmod a+r file.txt}} | ||
grants everyone on the cluster the right to read file.txt. | grants everyone on the cluster the right to read file.txt. | ||
<!--T:5--> | <!--T:5--> | ||
It's also common for people to use | It's also common for people to use <i>octal notation</i> when referring to Unix filesystem permissions even if this is somewhat less intuitive than the above symbolic notation. In this case, we use three bits to represent the permissions for each category of user, with these three bits then interpreted as a number from 0 to 7 using the formula (read_bit)*4 + (write_bit)*2 + (execute_bit)*1. In the above example, the octal representation would be 4+2+0 = 6 for the owner and 4+0+0 = 4 for the group and everyone else, so 644 overall. | ||
<!--T:6--> | <!--T:6--> | ||
| Line 41: | Line 44: | ||
<!--T:7--> | <!--T:7--> | ||
You can alter these permissions using the command < | You can alter these permissions using the command <code>chmod</code> in conjunction with the octal notation discussed above, so for example | ||
{{Command|chmod | {{Command|chmod 770 name_of_file}} | ||
means that everyone | means that everyone in your group now has the right to read, write and execute this file. Naturally, you can only modify the permissions of a file or directory you own. You can also alter the group by means of the command <code>chgrp</code>. | ||
===The | ===The sticky bit=== <!--T:13--> | ||
When dealing with a shared directory where multiple users have read, write and execute permission, as would be common in the [[Project_layout | project space]] for a professor with several active students and collaborators, the issue of ensuring that an individual cannot delete the files or directories of another can arise. For preventing this kind of behaviour the Unix filesystem developed the concept of the [https://en.wikipedia.org/wiki/Sticky_bit sticky bit] by means of which the filesystem permissions for a directory can be restricted so that a file in that directory can only be renamed or deleted by the file's owner or the directory's owner. Without this sticky bit, users with write and execute permission for that directory can rename or delete any files that it may contain even if they are not the file's owner. The sticky bit can be set using the command <code>chmod</code>, for example | When dealing with a shared directory where multiple users have read, write and execute permission, as would be common in the [[Project_layout | project space]] for a professor with several active students and collaborators, the issue of ensuring that an individual cannot delete the files or directories of another can arise. For preventing this kind of behaviour, the Unix filesystem developed the concept of the [https://en.wikipedia.org/wiki/Sticky_bit sticky bit] by means of which the filesystem permissions for a directory can be restricted so that a file in that directory can only be renamed or deleted by the file's owner or the directory's owner. Without this sticky bit, users with write and execute permission for that directory can rename or delete any files that it may contain even if they are not the file's owner. The sticky bit can be set using the command <code>chmod</code>, for example | ||
{{Command|chmod +t <directory name>}} | {{Command|chmod +t <directory name>}} | ||
or if you prefer to use the octal notation discussed above by using the mode 1000, hence | or if you prefer to use the octal notation discussed above by using the mode 1000, hence | ||
| Line 64: | Line 67: | ||
In the context of the project space, the directory owner will be the PI who sponsors the roles of the students and collaborators. | In the context of the project space, the directory owner will be the PI who sponsors the roles of the students and collaborators. | ||
=== Set Group ID | === Set Group ID bit === <!--T:16--> | ||
When creating files and directories within a parent directory it is often useful to match the group | When creating files and directories within a parent directory, it is often useful to match the group ownership of the new files or directories to the parent directory's owner or group automatically. This is key to the operation of the [[Project layout|Project]] filesystems at Graham and Cedar for example, since storage quotas in Project spaces are enforced by group. | ||
<!--T:18--> | <!--T:18--> | ||
If | If the <code>setGID</code> bit is enabled for a directory, new files and directories in that directory will be created with the same group ownership as the directory. To illustrate the use of this mode, let us walk through an example. | ||
<!--T:17--> | <!--T:17--> | ||
| Line 87: | Line 90: | ||
-rw-rw-r-- 1 someuser someuser 0 Oct 13 19:38 test01.txt | -rw-rw-r-- 1 someuser someuser 0 Oct 13 19:38 test01.txt | ||
</source> | </source> | ||
If we are in <code>/project</code> this is probably not what we want. We want a newly created file to belong to the same group as the parent folder. | If we are in <code>/project</code> this is probably not what we want. We want a newly created file to belong to the same group as the parent folder. Enable the <code>setGID</code> permission on the parent directory like so: | ||
<source lang="console"> | <source lang="console"> | ||
[someuser@server]$ chmod g+s dirTest | [someuser@server]$ chmod g+s dirTest | ||
| Line 100: | Line 103: | ||
-rw-rw-r-- 1 someuser def-someuser 0 Oct 13 19:39 test02.txt | -rw-rw-r-- 1 someuser def-someuser 0 Oct 13 19:39 test02.txt | ||
</source> | </source> | ||
If we create a directory inside a directory with the | If we create a directory inside a directory with the <code>setGID</code> enabled, it will have the same group as the parent folder and also have its <code>setGID</code> enabled. | ||
<source lang="console"> | <source lang="console"> | ||
[someuser@server]$ mkdir dirTest/dirChild | [someuser@server]$ mkdir dirTest/dirChild | ||
| Line 108: | Line 111: | ||
drwxrwsr-x 1 someuser def-someuser 0 Oct 13 19:39 dirChild | drwxrwsr-x 1 someuser def-someuser 0 Oct 13 19:39 dirChild | ||
</source> | </source> | ||
Finally it can be important to note the difference between | Finally, it can be important to note the difference between <code>S</code> (uppercase S) and <code>s</code>. The uppercase S indicates that execute permissions have been removed from the directory but the <code>setGID</code> is still in place. It can be easy to miss this and may result in unexpected problems, such as others in the group not being able to access files within your directory. | ||
<source lang="console"> | <source lang="console"> | ||
[someuser@server]$ chmod g-x dirTest/ | [someuser@server]$ chmod g-x dirTest/ | ||
| Line 114: | Line 117: | ||
drwxrS--- 3 someuser def-someuser 4096 Oct 13 19:39 dirTest | drwxrS--- 3 someuser def-someuser 4096 Oct 13 19:39 dirTest | ||
</source> | </source> | ||
=== Set User ID bit === <!--T:47--> | |||
The <code>setUID</code> bit <b>will not work</b> on our clusters. | |||
Its usual behaviour is completely disabled, for security reasons. | |||
== Default filesystem permissions == <!--T:39--> | == Default filesystem permissions == <!--T:39--> | ||
| Line 123: | Line 130: | ||
{{Command|prompt=[user@gra-login1]$|umask -S | {{Command|prompt=[user@gra-login1]$|umask -S | ||
|result=u=rwx,g=rx,o=}} | |result=u=rwx,g=rx,o=}} | ||
This means that, by default, new files that you create can be read, written and executed by yourself, they can be read and executed by members of the group of the file, and they cannot be accessed by other people. | This means that, by default, new files that you create can be read, written and executed by yourself, they can be read and executed by members of the group of the file, and they cannot be accessed by other people. <b>The <code>umask</code> only applies to new files. Changing the <code>umask</code> does not change the access permissions of existing files.</b> | ||
<!--T:41--> | <!--T:41--> | ||
| Line 154: | Line 161: | ||
=== Change of the default <code>umask</code> on Cedar, Béluga and Niagara === <!--T:44--> | === Change of the default <code>umask</code> on Cedar, Béluga and Niagara === <!--T:44--> | ||
In the summer 2019, we discovered that the default <code>umask</code> was not the same on all | In the summer 2019, we discovered that the default <code>umask</code> was not the same on all our servers. On October 16th, 2019, we changed the default <code>umask</code> on these three servers to match the one from Graham. The default <code>umask</code> changed as follows: | ||
{| class="wikitable" | {| class="wikitable" | ||
|- | |- | ||
| Line 169: | Line 176: | ||
<!--T:45--> | <!--T:45--> | ||
Note that this change does | Note that this change does <i>not</i> mean that your files have been inappropriately exposed in the past. Restrictive access permissions have been set on your home, project, and scratch directories since the beginning. Unless the permissions were changed to give <i>execute</i> permission to other users on these folders, they still cannot be accessed by them. | ||
=== Changing the permissions of existing files === <!--T:46--> | === Changing the permissions of existing files === <!--T:46--> | ||
| Line 179: | Line 186: | ||
== Access control lists (ACLs) == <!--T:10--> | == Access control lists (ACLs) == <!--T:10--> | ||
=== Sharing | === Sharing access with an individual === <!--T:25--> | ||
<!--T:8--> | <!--T:8--> | ||
The file permissions discussed above have been available in Unix-like operating systems for decades now but they are very coarse-grained. The whole set of users is divided into just three categories: the owner, the group, and everyone else. What if you want to allow someone who isn't in a group to read a file - do you really need to make the file readable by everyone in that case? The answer, happily, is no. | The file permissions discussed above have been available in Unix-like operating systems for decades now but they are very coarse-grained. The whole set of users is divided into just three categories: the owner, the group, and everyone else. What if you want to allow someone who isn't in a group to read a file - do you really need to make the file readable by everyone in that case? The answer, happily, is no. Our national systems offer <i>access control lists</i> (ACLs) to enable permissions to be set on a user-by-user basis if desired. The two commands needed to manipulate these extended permissions are | ||
* < | * <code>getfacl</code> to see the ACL permissions, and | ||
* < | * <code>setfacl</code> to alter them. | ||
==== Sharing a single file ==== <!--T:19--> | ==== Sharing a single file ==== <!--T:19--> | ||
To allow a single person with username < | To allow a single person with username <code>smithj</code> to have read and execute permission on the file <code>my_script.py</code>, use: | ||
<source lang="console"> | <source lang="console"> | ||
$ setfacl -m u:smithj:rx my_script.py | $ setfacl -m u:smithj:rx my_script.py | ||
| Line 199: | Line 206: | ||
<!--T:27--> | <!--T:27--> | ||
<source lang="console"> | <source lang="console"> | ||
$ setfacl -d -m u:smithj: | $ setfacl -d -m u:smithj:rwX /home/<user>/projects/def-<PI>/shared_data | ||
$ setfacl -R -m u:smithj: | $ setfacl -R -m u:smithj:rwX /home/<user>/projects/def-<PI>/shared_data | ||
</source> | </source> | ||
; Note: The X attribute above (compared to x) sets the <i>execute</i> permission only when the item is already executable (either a directory or a file with the execute permission). A directory needs the execute permission to allow it to be browsed. | |||
<!--T:28--> | <!--T:28--> | ||
The first command sets default access rules to directory <code>/home/<user>/projects/def-<PI>/shared_data</code>, so any file or directory created within it will inherit the same ACL rule. It is required for | The first command sets default access rules to directory <code>/home/<user>/projects/def-<PI>/shared_data</code>, so any file or directory created within it will inherit the same ACL rule. It is required for <b>new</b> data. The second command sets ACL rules to directory <code>/home/<user>/projects/def-<PI>/shared_data</code> and all its content currently in it. So it is applicable only to <b>existing</b> data. | ||
<!--T:29--> | <!--T:29--> | ||
In order for this method to work the following things need to be in place: | In order for this method to work the following things need to be in place: | ||
* The directory, <code>/home/smithj/projects/def-smithj/shared_data</code> in our example, must be owned by you. | * The directory, <code>/home/smithj/projects/def-smithj/shared_data</code> in our example, must be owned by you. | ||
* Parent directories (and parents of parents, etc.) of the one you are trying to share must allow execute permission to the user you are trying to share with. | * Parent directories (and parents of parents, etc.) of the one you are trying to share must allow execute permission to the user you are trying to share with. This can be supplied with <code>setfacl -m u:smithj:X ...</code> in this example, or it can be supplied by allowing everyone entry, i.e. <code>chmod o+x ...</code>. They do not need to have public read permission. In particular you will need to grant execute permission on the project directory (<code>/projects/def-<PI></code>) either for everyone, or one-by-one to all the people you are trying to share your data with. | ||
* When sharing a directory in the project filesystem, you must provide your collaborators with a path that starts with <code>/project</code>, <b>not</b> with <code>/home/<user>/projects</code>. The latter contains symbolic links (symlinks, or shortcuts) to the physical directories in <code>/project</code>, and these symlinks will not be reachable by your collaborators unless they also have access to your home directory. You can get the physical path a symlink points to using the <code>realpath</code> command. For example, <code>realpath /home/smithj/projects/def-smithj/shared_data</code> could return <code>/project/9041430/shared_data</code>. The physical path to a project directory is not the same on all clusters. If you wish to share a project directory on more than one cluster, check its physical path with <code>realpath</code> on each cluster. | |||
==== Removing ACL ==== <!--T:48--> | |||
To remove all extended ACL attributes from a directory recursively, use: | |||
<source lang="console"> | |||
setfacl -bR /home/<user>/projects/def-<PI>/shared_data | |||
</source> | |||
=== Data | === Data sharing groups === <!--T:30--> | ||
<!--T:31--> | <!--T:31--> | ||
For more complicated data sharing scenarios (those involving multiple people on multiple clusters), it is also possible to create a | For more complicated data sharing scenarios (those involving multiple people on multiple clusters), it is also possible to create a <b>data sharing group</b>. A data sharing group is a special group to which all people with whom certain data is to be shared are added. This group is then given access permissions through ACLs. | ||
<!--T:32--> | <!--T:32--> | ||
| Line 225: | Line 240: | ||
<!--T:34--> | <!--T:34--> | ||
<br />1. Send email to [ | <br />1. Send email to our [[technical support]] requesting creation of data sharing group, indicate name of the group you would like to have and that you should be the owner. | ||
<br />2. When you receive confirmation from | <br />2. When you receive confirmation from the technical support team that the group has been created, go to [https://ccdb.computecanada.ca/services/ ccdb.computecanada.ca/services/] and access it:<br /> | ||
[[File:Cc services screen.png|1036px|Services screen displaying groups you can manage]] | [[File:Cc services screen.png|1036px|Services screen displaying groups you can manage]] | ||
| Line 247: | Line 262: | ||
or | or | ||
<source> | <source> | ||
$ setfacl g:wg_datasharing:X /project/def-<PI>/ | $ setfacl -m g:wg_datasharing:X /project/def-<PI>/ | ||
</source> | </source> | ||
Latest revision as of 21:32, 15 September 2023
Parent page: Storage and file management
IMPORTANT NOTE: Don't ever issue a bulk chmod -R 777 on your home folder, in fact on any of your folders for that matter. This is a HUGE security risk, and is completely unacceptable on shared facilities such as our clusters. In addition, it's never necessary.
Having to share some but not all of your data with a colleague or another research group is a common occurrence. Our systems provide a variety of mechanisms to facilitate this data sharing with colleagues. If the person you want to share the data with is a member of the same research group as you, then the best approach may be to make use of the project space that each research group has in common; if your research requires the creation of a group on one of the national clusters, you can request this by contacting technical support since users cannot create their own groups. At the opposite extreme, if the person you need to share the data with doesn't even have an account on the cluster, you can use Globus and in particular what is called a shared endpoint to share the data. To handle the scenario of sharing with a colleague who has an account on the cluster but doesn't belong to a common research group with you, the simplest approach is to use the permissions available in the filesystem to share the data, the principal topic of this page.
When sharing a file, it's important to realize that the individual you want to share it with must have access to the entire chain of directories leading from /scratch or /project to the directory in which the file is located. If we consider the metaphor of a document locked in a safe in the bedroom of your apartment in a large building, giving me the combination to the safe will not allow me to read this document if I do not also have the necessary keys to enter the apartment building, your apartment and finally your bedroom. In the context of a filesystem, this means having execute permission for each directory between the root (e.g. /scratch or /project) and the directory containing the file.
Filesystem permissions
Like most modern filesystems, those used on our clusters support the idea of permissions to read, write, and execute files and directories. When you attempt to read, modify or delete a file, or access a directory, e.g. with cd, the Linux kernel first verifies that you have the right to do this. If not, you'll see the error message Permission denied. For each filesystem object (file or directory) there are three categories of users:
- the object's owner --- normally the user who created the object,
- members of the object's group --- normally the same as the owner's default group, and
- everyone else.
Each of these categories of users may have the right to read, write, or execute the object. Three categories of users times three types of permission means there are nine permissions associated with each object.
You can see what the current permissions are for a filesystem object with the command
[name@server ~]$ ls -l name_of_object
which will print out the permissions for the owner, the group, and everyone else. For example, a file with permissions ‑rw‑r‑‑r‑‑ means the owner can read it and write it but not execute it, and the group members and everyone else can only read the file. You'll also see printed out the name of the object's owner and the group.
To change the permissions of a file or directory you can use the command chmod along with the user category, a plus or minus sign indicating that permission is granted or withdrawn, and the nature of the permission: read (r), write (w) or execute (x). For the user category, we use the abbreviations u for the owner (user), g for the group and o for others, i.e. everyone else on the cluster. So a command like
[name@server ~]$ chmod g+r file.txt
would grant read permission to all members of the group that file.txt belongs to, while
[name@server ~]$ chmod o-x script.py
would withdraw execute permission for the file script.py to everyone but the owner and the group. We can also use the user category a to denote everyone (all), thus
[name@server ~]$ chmod a+r file.txt
grants everyone on the cluster the right to read file.txt.
It's also common for people to use octal notation when referring to Unix filesystem permissions even if this is somewhat less intuitive than the above symbolic notation. In this case, we use three bits to represent the permissions for each category of user, with these three bits then interpreted as a number from 0 to 7 using the formula (read_bit)*4 + (write_bit)*2 + (execute_bit)*1. In the above example, the octal representation would be 4+2+0 = 6 for the owner and 4+0+0 = 4 for the group and everyone else, so 644 overall.
Note that to be able to exercise your rights on a file, you also need to be able to access the directory in which it resides. This means having both read and execute permission ("5" or "7" in octal notation) on the directory in question.
You can alter these permissions using the command chmod in conjunction with the octal notation discussed above, so for example
[name@server ~]$ chmod 770 name_of_file
means that everyone in your group now has the right to read, write and execute this file. Naturally, you can only modify the permissions of a file or directory you own. You can also alter the group by means of the command chgrp.
The sticky bit
When dealing with a shared directory where multiple users have read, write and execute permission, as would be common in the project space for a professor with several active students and collaborators, the issue of ensuring that an individual cannot delete the files or directories of another can arise. For preventing this kind of behaviour, the Unix filesystem developed the concept of the sticky bit by means of which the filesystem permissions for a directory can be restricted so that a file in that directory can only be renamed or deleted by the file's owner or the directory's owner. Without this sticky bit, users with write and execute permission for that directory can rename or delete any files that it may contain even if they are not the file's owner. The sticky bit can be set using the command chmod, for example
[name@server ~]$ chmod +t <directory name>
or if you prefer to use the octal notation discussed above by using the mode 1000, hence
[name@server ~]$ chmod 1774 <directory name>
to set the sticky bit and rwxrwxr-- permissions on the directory.
The sticky bit is represented in ls -l output by the letter "t" or "T" in the last place of the permissions field, like so:
$ ls -ld directory drwxrws--T 2 someuser def-someuser 4096 Sep 25 11:25 directory
The sticky bit can be unset by the command
[name@server ~]$ chmod -t <directory name>
or via octal notation,
[name@server ~]$ chmod 0774 <directory name>
In the context of the project space, the directory owner will be the PI who sponsors the roles of the students and collaborators.
Set Group ID bit
When creating files and directories within a parent directory, it is often useful to match the group ownership of the new files or directories to the parent directory's owner or group automatically. This is key to the operation of the Project filesystems at Graham and Cedar for example, since storage quotas in Project spaces are enforced by group.
If the setGID bit is enabled for a directory, new files and directories in that directory will be created with the same group ownership as the directory. To illustrate the use of this mode, let us walk through an example.
Start by checking the groups that someuser belongs to with the groups command.
[someuser@server]$ groups
someuser def-someuser
someuser belongs to two groups someuser and def-someuser. In the current working directory there is a directory which belongs to the group def-someuser.
[someuser@server]$ ls -l
drwxrwx--- 2 someuser def-someuser 4096 Oct 13 19:39 testDir
If we create a new file in that directory we can see that it is created belonging to someuser's default group someuser.
[someuser@server]$ touch dirTest/test01.txt
[someuser@server]$ ls -l dirTest/
-rw-rw-r-- 1 someuser someuser 0 Oct 13 19:38 test01.txt
If we are in /project this is probably not what we want. We want a newly created file to belong to the same group as the parent folder. Enable the setGID permission on the parent directory like so:
[someuser@server]$ chmod g+s dirTest
[someuser@server]$ ls -l
drwxrws--- 2 someuser def-someuser 4096 Oct 13 19:39 dirTest
Notice that the x permission on the group permissions has changed to an s. Now newly created files in dirTest will have the same group as the parent directory.
[someuser@server]$ touch dirTest/test02.txt
[someuser@server]$ ls -l dirTest
-rw-rw-r-- 1 someuser someuser 0 Oct 13 19:38 test01.txt
-rw-rw-r-- 1 someuser def-someuser 0 Oct 13 19:39 test02.txt
If we create a directory inside a directory with the setGID enabled, it will have the same group as the parent folder and also have its setGID enabled.
[someuser@server]$ mkdir dirTest/dirChild
[someuser@server]$ ls -l dirTest/
-rw-rw-r-- 1 someuser someuser 0 Oct 13 19:38 test01.txt
-rw-rw-r-- 1 someuser def-someuser 0 Oct 13 19:39 test02.txt
drwxrwsr-x 1 someuser def-someuser 0 Oct 13 19:39 dirChild
Finally, it can be important to note the difference between S (uppercase S) and s. The uppercase S indicates that execute permissions have been removed from the directory but the setGID is still in place. It can be easy to miss this and may result in unexpected problems, such as others in the group not being able to access files within your directory.
[someuser@server]$ chmod g-x dirTest/
[someuser@server]$ ls -l
drwxrS--- 3 someuser def-someuser 4096 Oct 13 19:39 dirTest
Set User ID bit
The setUID bit will not work on our clusters.
Its usual behaviour is completely disabled, for security reasons.
Default filesystem permissions
Default filesystem permissions are defined by something called the umask. There is a default value that is defined on any Linux system. To display the current value in your session, you can run the command
[name@server ~]$ umask -S
For example, on Graham, you would get
[user@gra-login1]$ umask -S
u=rwx,g=rx,o=
This means that, by default, new files that you create can be read, written and executed by yourself, they can be read and executed by members of the group of the file, and they cannot be accessed by other people. The umask only applies to new files. Changing the umask does not change the access permissions of existing files.
There may be reasons to define default permissions more permissive (for example, to allow other people to read and execute files), or more restrictive (not allowing your group to read or execute files). Setting your own umask can be done either in a session, or in your .bashrc file, by calling the command
[name@server ~]$ umask <value>
where the <value> can take a number of octal values. Below is a table of useful options, depending on your use case :
umask value |
umask meaning |
Human-readable explanation |
|---|---|---|
| 077 | u=rwx,g=,o= | Files are readable, writable and executable by the owner only |
| 027 | u=rwx,g=rx,o= | Files are readable and executable by the owner and the group, but writable only by the owner |
| 007 | u=rwx,g=rwx,o= | Files are readable, writable and executable by the owner and the group |
| 022 | u=rwx,g=rx,o=rx | Files are readable and executable by everyone, but writable only by the owner |
| 002 | u=rwx,g=rwx,o=rx | Files are readable and executable by everyone, but writable only by the owner and the group |
The umask is not the only thing that determines who can access a file.
- A user trying to access a file must have execute permission on all directories in the path to the file. For example, a file might have
o=rxpermissions but an arbitrary user could not read or execute it if the parent directory does not also haveo=xpermission. - The user trying to access a file based on its group permissions must be a member of the file's group.
- You can explicitly change the permissions on a file or directory after it is created, using
chmod. - Access Control Lists (ACLs) also determine who can access a file.
Change of the default umask on Cedar, Béluga and Niagara
In the summer 2019, we discovered that the default umask was not the same on all our servers. On October 16th, 2019, we changed the default umask on these three servers to match the one from Graham. The default umask changed as follows:
| Cluster | umask before the change |
umask after the change
|
|---|---|---|
| Béluga | 002 | 027 |
| Cedar | 002 | 027 |
| Niagara | 022 | 027 |
This means that more restrictive permissions are enforced on newly created files. If you need more permissive permissions for your workflow, you can change your default umask in your .bashrc. Our general advice is however to keep the default permissions.
Note that this change does not mean that your files have been inappropriately exposed in the past. Restrictive access permissions have been set on your home, project, and scratch directories since the beginning. Unless the permissions were changed to give execute permission to other users on these folders, they still cannot be accessed by them.
Changing the permissions of existing files
If you want to change the permissions of existing files to match the new default permissions, you can use the chmod command as follow:
[name@server ~]$ chmod g-w,o-rx <file>
or, if you want to do it for a whole directory, you can run
[name@server ~]$ chmod -R g-w,o-rx <directory>
Access control lists (ACLs)
Sharing access with an individual
The file permissions discussed above have been available in Unix-like operating systems for decades now but they are very coarse-grained. The whole set of users is divided into just three categories: the owner, the group, and everyone else. What if you want to allow someone who isn't in a group to read a file - do you really need to make the file readable by everyone in that case? The answer, happily, is no. Our national systems offer access control lists (ACLs) to enable permissions to be set on a user-by-user basis if desired. The two commands needed to manipulate these extended permissions are
getfaclto see the ACL permissions, andsetfaclto alter them.
Sharing a single file
To allow a single person with username smithj to have read and execute permission on the file my_script.py, use:
$ setfacl -m u:smithj:rx my_script.py
Sharing a subdirectory
To allow read and write access to a single user in a whole subdirectory, including new files created in it, you can run the following commands:
$ setfacl -d -m u:smithj:rwX /home/<user>/projects/def-<PI>/shared_data
$ setfacl -R -m u:smithj:rwX /home/<user>/projects/def-<PI>/shared_data
- Note
- The X attribute above (compared to x) sets the execute permission only when the item is already executable (either a directory or a file with the execute permission). A directory needs the execute permission to allow it to be browsed.
The first command sets default access rules to directory /home/<user>/projects/def-<PI>/shared_data, so any file or directory created within it will inherit the same ACL rule. It is required for new data. The second command sets ACL rules to directory /home/<user>/projects/def-<PI>/shared_data and all its content currently in it. So it is applicable only to existing data.
In order for this method to work the following things need to be in place:
- The directory,
/home/smithj/projects/def-smithj/shared_datain our example, must be owned by you. - Parent directories (and parents of parents, etc.) of the one you are trying to share must allow execute permission to the user you are trying to share with. This can be supplied with
setfacl -m u:smithj:X ...in this example, or it can be supplied by allowing everyone entry, i.e.chmod o+x .... They do not need to have public read permission. In particular you will need to grant execute permission on the project directory (/projects/def-<PI>) either for everyone, or one-by-one to all the people you are trying to share your data with. - When sharing a directory in the project filesystem, you must provide your collaborators with a path that starts with
/project, not with/home/<user>/projects. The latter contains symbolic links (symlinks, or shortcuts) to the physical directories in/project, and these symlinks will not be reachable by your collaborators unless they also have access to your home directory. You can get the physical path a symlink points to using therealpathcommand. For example,realpath /home/smithj/projects/def-smithj/shared_datacould return/project/9041430/shared_data. The physical path to a project directory is not the same on all clusters. If you wish to share a project directory on more than one cluster, check its physical path withrealpathon each cluster.
Removing ACL
To remove all extended ACL attributes from a directory recursively, use:
setfacl -bR /home/<user>/projects/def-<PI>/shared_data
Data sharing groups
For more complicated data sharing scenarios (those involving multiple people on multiple clusters), it is also possible to create a data sharing group. A data sharing group is a special group to which all people with whom certain data is to be shared are added. This group is then given access permissions through ACLs.
You do not need a data sharing group except in specialized sharing circumstances.
Creating a data sharing group
The steps below describe how to create a data sharing group. In this example it is called wg-datasharing
1. Send email to our technical support requesting creation of data sharing group, indicate name of the group you would like to have and that you should be the owner.
2. When you receive confirmation from the technical support team that the group has been created, go to ccdb.computecanada.ca/services/ and access it:
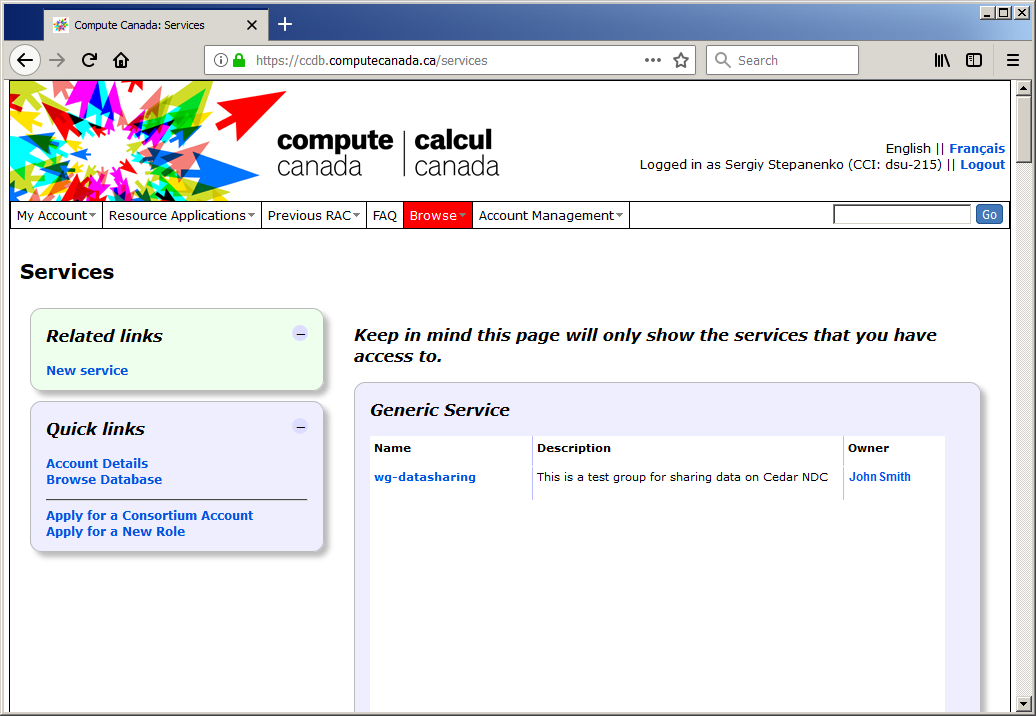
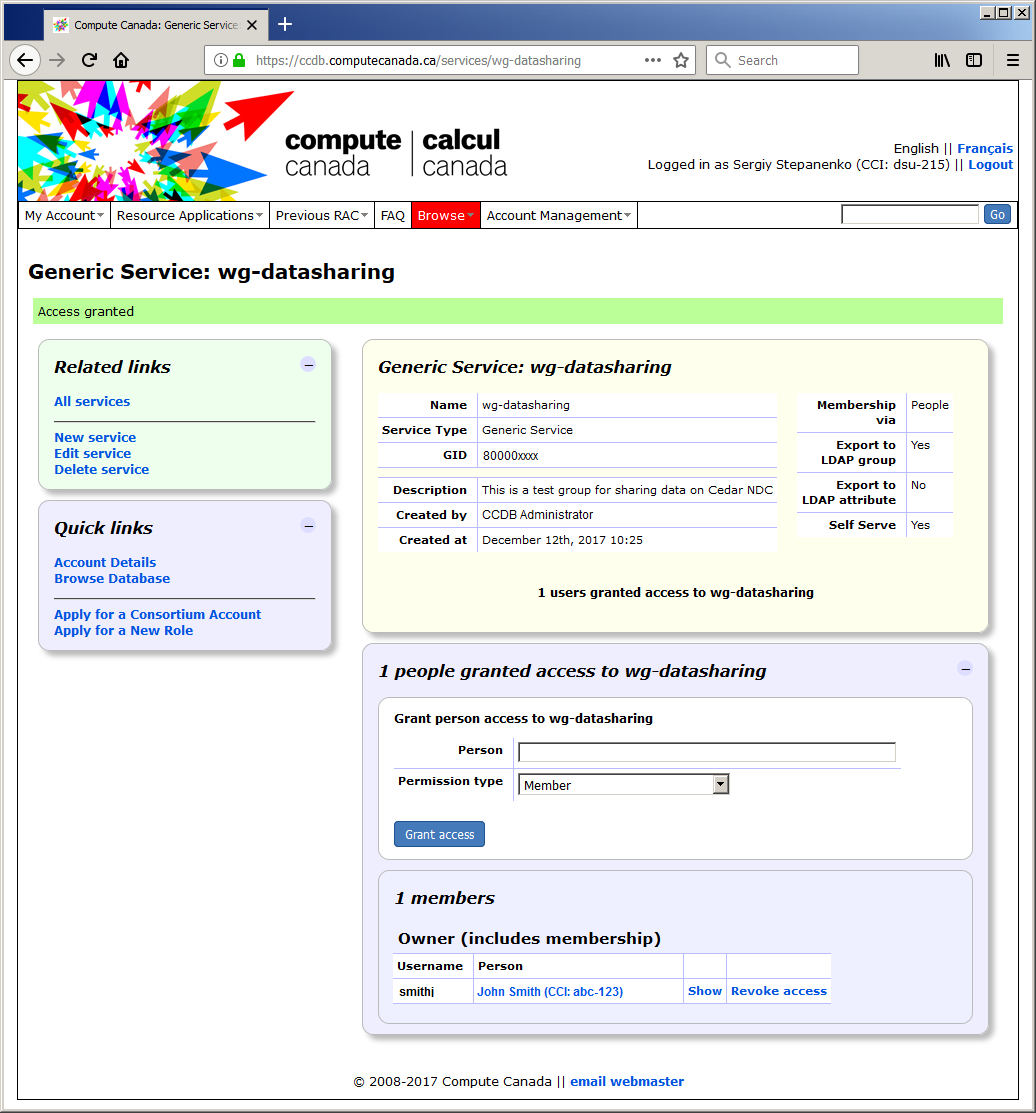
3. Click on the group's name and enter the group management screen:
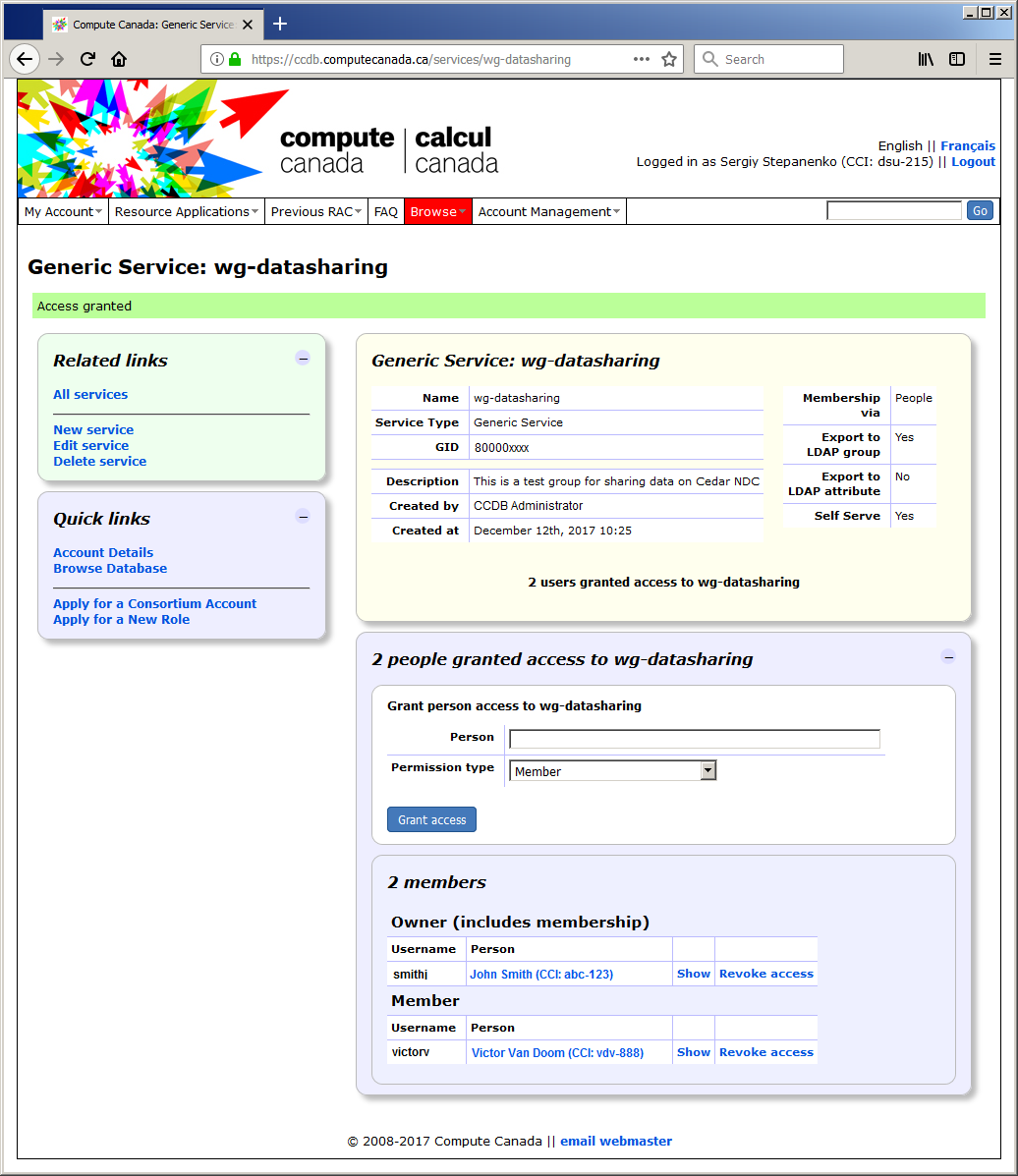
4. Add member (Victor Van Doom with CCI vdv-888, for example) to the group as a member:
Using a data sharing group
Just as with individual user sharing, the parent directories of the data you are trying to share must have execute permissions either for everyone or for the data sharing group. In your project directory, this implies that your PI must give consent as follows (unless you have permission to do this yourself):
$ chmod o+X /project/def-<PI>/or
$ setfacl -m g:wg_datasharing:X /project/def-<PI>/Finally, you can add your group to the ACL for the directory you are trying to share. The commands parallel those needed to share with an individual:
$ setfacl -d -m g:wg-datasharing:rwx /home/<user>/projects/def-<PI>/shared_data
$ setfacl -R -m g:wg-datasharing:rwx /home/<user>/projects/def-<PI>/shared_data